Understanding administrators
Depending on their role, administrators in Sectigo Certificate Manager (SCM) are responsible for certificate lifecycle management, policy enforcement, access control, and ensuring organizational compliance. They ensure certificates are managed securely, issued accurately, and are aligned with industry standards and regulations.
The primary administrator privileges and restrictions are divided as follows:
-
MRAO administrator — A Master Registration Authority Officer (MRAO) administrator can make changes across all organizations and departments in an enterprise account without any restrictions.
-
RAO administrator — A Registration Authority Officer (RAO) administrator can perform operations on specific organizations and departments and for specific certificate types.
-
DRAO administrator — A Department Registration Authority Officer (DRAO) can only perform operations on specific departments and for specific certificate types.
Administrators can be managed on the page.
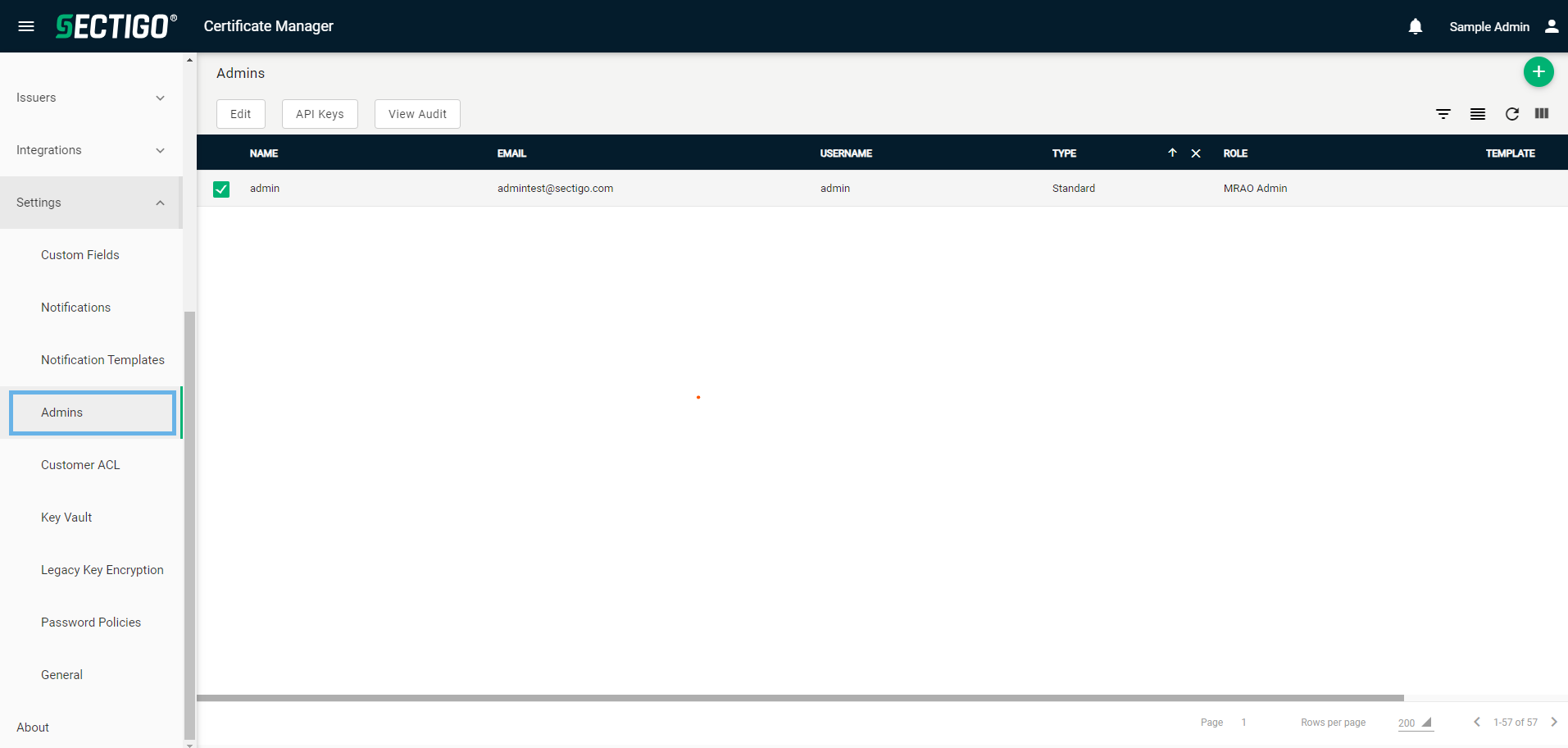
The following table describes the details and controls of the Admins page.
| Column | Description |
|---|---|
Name |
The administrator’s full name. |
The administrator’s email address used for notifications and certificate issuance. |
|
Username |
The Standard or API administrator’s user name. |
Type |
The type of administrator:
|
Role |
The specific role of the administrator:
|
Template |
Indicates the IdP and dynamic IdP templates used to create the IdP user. |
Active |
Indicates whether the administrator account is active and able to access SCM. |
Table controls |
|
Quick Search |
Enables you to quickly search the results by ID, Name, Email, or Username. |
Filter |
Enables you to sort the table information using custom filters. |
Group |
Enables you to sort the table information using predefined groups. |
Refresh |
Refreshes the information presented in the table. |
Manage Columns |
Enables you to select which table columns to display. |
Admin controls |
|
Add |
Opens the Add Admin dialog where you can add a new administrator account. |
Delete |
Removes the selected administrator profile. |
Edit |
Opens the Edit Admin dialog where you can manage an existing certificate profile. |
API Keys |
Opens the API Keys dialog where you can add or edit admin API keys. |
Change Type |
Opens the Edit Admin Type dialog where you can change the administrator from one type to another. |
Send IdP Invitation |
Sends an email to the administrator that they can use to connect their SCM account to an available IdP. |
Resend IdP Invitation |
Resends the email to the administrator that they can use to complete the connection of their SCM account to an available IdP. |
View Audit |
Opens the Profile Audit dialog where you can view or download audit logs. |
Activate/Deactivate |
Located in the Active column, the selector enables you to switch administrators between active and inactive status. |
Comparing administrator roles
Administrators can be configured with specific privileges as needed. The privileges available for selection are determined by the administrator’s role and the certificate types that they are authorized to manage.
The following table lists all potential privileges for the various administrative roles.
| Privilege | MRAO | RAO | DRAO |
|---|---|---|---|
General privileges |
|||
Add peer administrator |
✓ |
✓ |
✓ |
Edit peer administrator |
✓ |
✓ |
✓ |
Delete peer administrator |
✓ |
✓ |
✓ |
Automatically approve certificate requests |
✓ |
✓ |
✓ |
MS agent management |
✓ |
✗ |
✗ |
Download keys from Sectigo Key Vault |
✓ |
✓ |
✓ |
Accept customer license agreements |
✓ |
✗ |
✗ |
Domain privileges |
|||
Manage domain validations |
✓ |
✓ |
✓ |
Manage domains |
✓ |
✓ |
✓ |
Approve domain delegations |
✓ |
✓ |
✗ |
SSL certificate privileges |
|||
Request SSL certificates |
✓ |
✓ |
✓ |
Renew SSL certificates |
✓ |
✓ |
✓ |
Replace SSL certificates |
✓ |
✓ |
✓ |
Revoke SSL certificates |
✓ |
✓ |
✓ |
Manage SSL certificate requests |
✓ |
✓ |
✓ |
Manage SSL certificates |
✓ |
✓ |
✓ |
Import SSL certificates |
✓ |
✓ |
✓ |
Client certificate privileges |
|||
Request client certificates |
✓ |
✓ |
✓ |
Revoke client certificates |
✓ |
✓ |
✓ |
Manage client certificates |
✓ |
✓ |
✓ |
Import SSL certificates |
✓ |
✓ |
✓ |
Code signing certificate privileges |
|||
Request code signing certificates |
✓ |
✓ |
✓ |
Revoke code signing certificates |
✓ |
✓ |
✓ |
Manage code signing certificates |
✓ |
✓ |
✓ |
Import SSL certificates |
✓ |
✓ |
✓ |
Device certificate privileges |
|||
Request device certificates |
✓ |
✓ |
✓ |
Renew device certificates |
✓ |
✓ |
✓ |
Replace device certificates |
✓ |
✓ |
✓ |
Revoke device certificates |
✓ |
✓ |
✓ |
Manage device certificate requests |
✓ |
✓ |
✓ |
Manage device certificates |
✓ |
✓ |
✓ |
Import SSL certificates |
✓ |
✓ |
✓ |
Custom field privileges |
|||
View custom fields |
✓ |
✓ |
✓ |
Add custom fields |
✓ |
✓ |
✓ |
Manage custom fields |
✓ |
✓ |
✓ |
Mark certificate privileges |
|||
Request mark certificates |
✓ |
✓ |
✓ |
Revoke mark certificates |
✓ |
✓ |
✓ |
Manage mark certificate requests |
✓ |
✓ |
✓ |
Manage mark certificates |
✓ |
✓ |
✓ |
Organizational privileges |
|||
Add organizations & departments |
✓ |
✗ |
✗ |
Manage organizations & departments |
✓ |
✗ |
✗ |
Add departments |
✗ |
✓ |
✗ |
Manage departments |
✗ |
✓ |
✗ |
Manage organization validations |
✓ |
✓ |
✗ |
Usage and billing privileges |
|||
View usage |
✓ |
✓ |
✓ |
View subscriptions |
✓ |
✓ |
✓ |
Manage subscriptions |
✓ |
✓ |
✓ |
Certificate profile privileges |
|||
View certificate profiles |
✓ |
✓ |
✓ |
Add certificate profiles |
✓ |
✓ |
✓ |
Manage certificate profiles |
✓ |
✓ |
✓ |