Understanding access restrictions
The Access Restrictions page enables you to limit incoming access to SCM to specific IP addresses and ranges by creating global and organization or department specific access restrictions. After creating a restriction by specifying one or more IP addresses or ranges in CIDR notation, only administrators attempting to log in from the specified addresses are granted access to SCM. Anyone who is blocked from accessing SCM because of a restriction is presented with a generic 403 Access Denied error.
Access restrictions can be managed on the page.
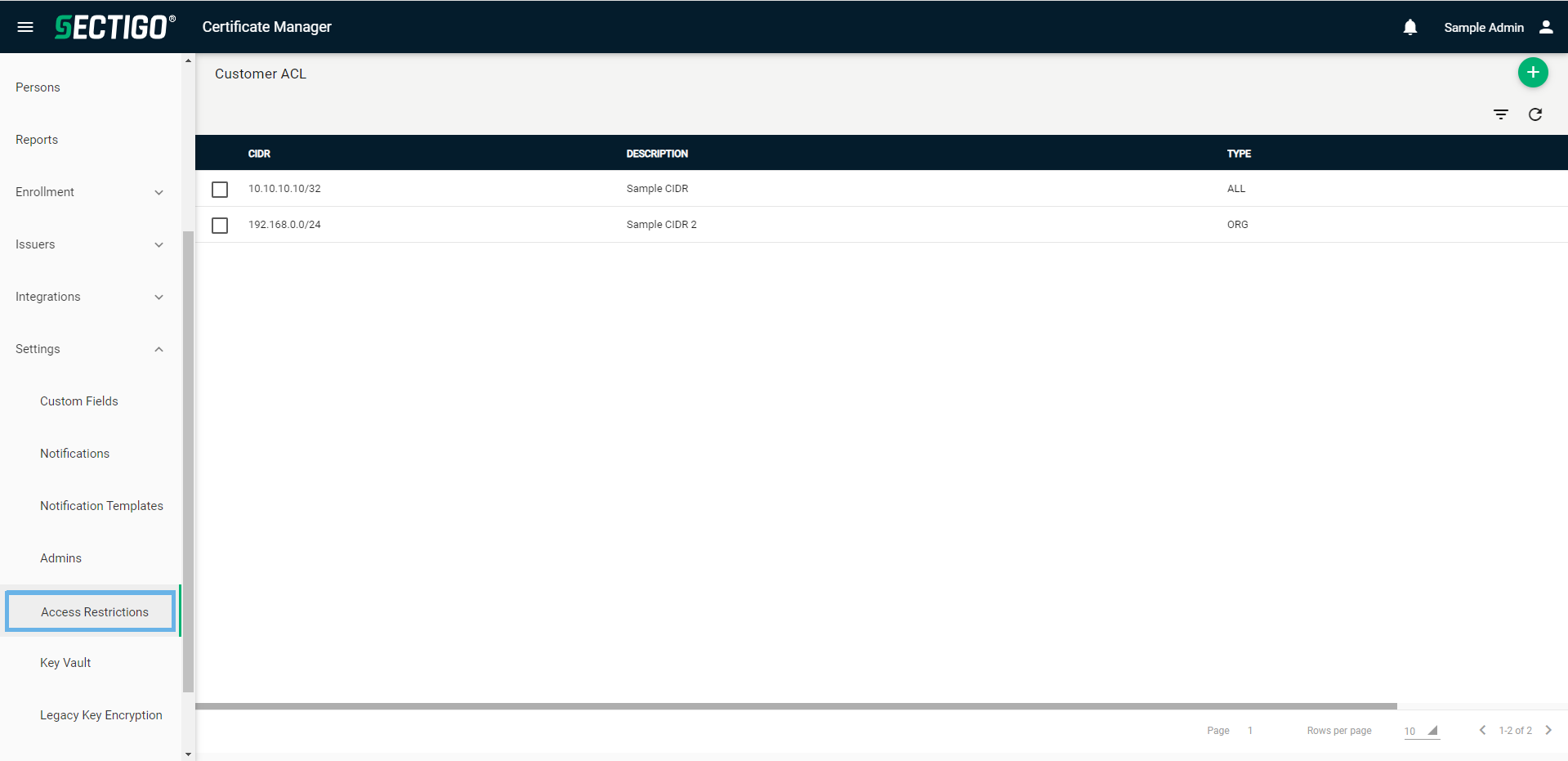
The following table describes the details and controls of the Access Restrictions page.
| Column | Description |
|---|---|
CIDR |
The IP address or range in CIDR notation to which SCM access is restricted. |
Description |
A description containing contextual information about the restriction. When creating a restriction for a specific organization or department, it is suggested that you include the organization or department name in the description. |
Type |
The type of administrator that the restriction applies to. The possible options are:
|
Table controls |
|
Filter |
Enables you to sort the table information using custom filters. |
Refresh |
Refreshes the information presented in the table. |
Admin controls |
|
Add |
Opens the Add IP Range dialog where you can add a new restriction. |
Delete |
Removes the selected restriction. |
Edit |
Opens the Edit IP Range dialog where you can manage an existing restriction. |