Using the connector
You can enroll and optionally install a certificate on a web server using Certbot with specific actions. To perform these actions, Cerbot uses a selection of authenticator and installer plugins.
Authenticator plugins automatically perform the steps to prove that you control the domain names you’re trying to request a certificate for. Installer plugins automatically modify your web server’s configuration to install a certificate and enable SSL. For more information about Certbot plugins, see choosing plugins.
The following table provides a subset of common Certbot commands. A complete list of Certbot commands can be found in Certbot documentation.
| Option | Description |
|---|---|
|
Registers a Sectigo ACME account |
|
Initiates the enrollment of a certificate |
|
Enrolls and installs a certificate to your current web server |
|
The ACME server URL for DV/EV/OV SSL certificates |
|
Indicates the domains to be included. Multiple domains can be added with additional domain options. The first domain value is added to the Common Name of the certificate, and all the other domain names are added to the Subject Alternative Name (SAN) field. |
|
Renews all enrolled certificates that are near expiry |
|
Revokes a certificate regardless of the remaining time until expiration |
|
Renews a certificate regardless of the remaining time until expiration |
|
Updates an existing certificate with a new certificate to include one or more additional domains |
|
Runs the command line without requesting further user input.
This may require the addition of other commands, such as |
|
Indicates that you agree to the Sectigo ACME terms of service |
|
The key ID for external account binding |
|
The HMAC key for external account binding |
|
The certificate name. This value is used as part of the certificate store path.
For example, if you specify |
|
Unregisters an SCM ACME account. Once unregistered, the ACME account is deactivated on the ACME server and cannot be restored. |
Enroll a certificate
The following sample commands perform some of the most commonly-used actions.
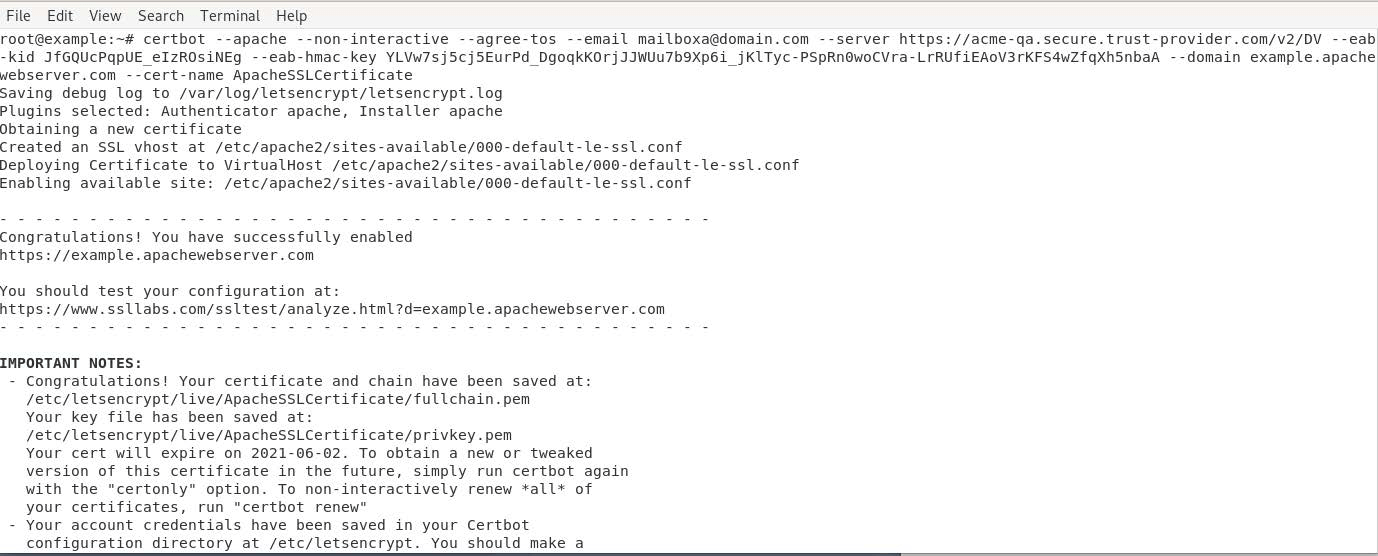
certbot certonly --standalone --non-interactive --agree-tos --email <[email protected]> --server <https://acme-qa.secure.trust-provider.com/v2/DV> --eab-kid <JfGQUcPqpUE_eIzROsiNEg> --eab-hmac-key <YLVw7sj5cj5EurPd_DgoqkKOrjJJWUu7b9Xp6i_jKlTyc-PSpRn0woCVra-LrRUfiEAoV3rKFS4wZfqXh5nbaA> --domain <example.com> --cert-name <example.com>certbot certonly --standalone --non-interactive --agree-tos --email <[email protected]> --server <https://acme-qa.secure.trust-provider.com/v2/DV> --eab-kid <JfGQUcPqpUE_eIzROsiNEg> --eab-hmac-key <YLVw7sj5cj5EurPd_DgoqkKOrjJJWUu7b9Xp6i_jKlTyc-PSpRn0woCVra-LrRUfiEAoV3rKFS4wZfqXh5nbaA> --domain <example.com> --domain <www.example.com> --domain <blog.example.com> --cert-name <example.com>certbot --apache --non-interactive --agree-tos --email <[email protected]> --server <https://acme-qa.secure.trust-provider.com/v2/DV> --eab-kid <JfGQUcPqpUE_eIzROsiNEg> --eab-hmac-key <YLVw7sj5cj5EurPd_DgoqkKOrjJJWUu7b9Xp6i_jKlTyc-PSpRn0woCVra-LrRUfiEAoV3rKFS4wZfqXh5nbaA> --domain <example.com> --cert-name <example.com>certbot --apache --non-interactive --agree-tos --email <[email protected]> --server <https://acme-qa.secure.trust-provider.com/v2/DV> --eab-kid <JfGQUcPqpUE_eIzROsiNEg> --eab-hmac-key <YLVw7sj5cj5EurPd_DgoqkKOrjJJWUu7b9Xp6i_jKlTyc-PSpRn0woCVra-LrRUfiEAoV3rKFS4wZfqXh5nbaA> --domain <example.com> --domain <www.example.com> --domain <blog.example.com> --cert-name <example.com>The certificate is successfully created and installed on the Apache web server.
certbot certonly --force-renewal --apache --non-interactive --agree-tos --email <[email protected]> --server <https://acme-qa.secure.trust-provider.com/v2/DV> --domain <example.com> --cert-name <example.com>certbot certonly --duplicate --apache --non-interactive --agree-tos --email <[email protected]> --server <https://acme-qa.secure.trust-provider.com/v2/DV> --domain <example.com> --cert-name <example.com>certbot revoke --cert-path /etc/letsencrypt/archive/<example.com>/cert1.pem -reason unspecifiedcertbot unregister --domain example.com -account <account_id>|
The account ID that you pass to |
Enable auto-renewal
You can create a cronjob that will invoke Cerbot on a schedule to check the certificate expiry status and renew the certificate automatically during the renewal period (see crontab for cron schedule expressions).
A cronfile is automatically added to /etc/cron.d/certbot during Certbot installation.
Update the contents of the cronfile appropriately.
The following example will trigger Certbot every week (the -q option prevents all output except errors).
SHELL=/bin/sh
PATH=/usr/local/sbin:/usr/local/bin:/sbin:/bin:/usr/sbin:/usr/bin
0 0 * * 7 root certbot -q renew --apacheVerify the enrollment of SSL certificates Apache
-
Navigate to the
etc/letsencryptdirectory to view the registered ACME account information and corresponding certificates and keys.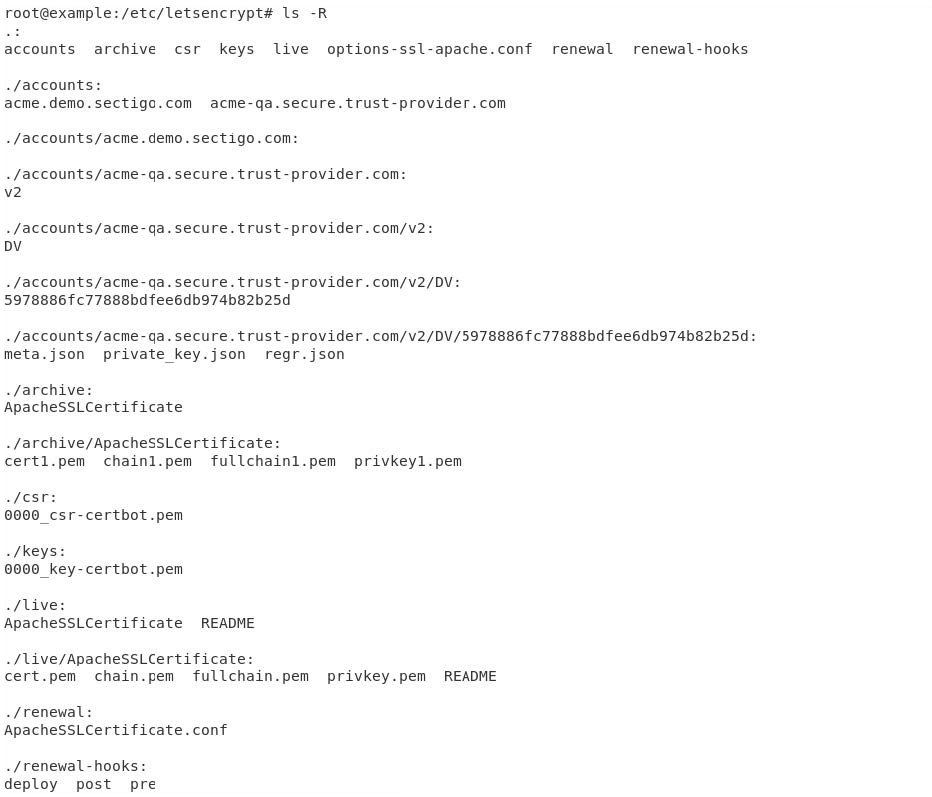
-
Connect to the Apache web server through port
443using the OpenSSLs_clientcommand to verify the SSL status.The following image confirms that an SSL certificate is installed on the Apache server and the website is enabled with SSL.
openssl s_client -connect example.com:443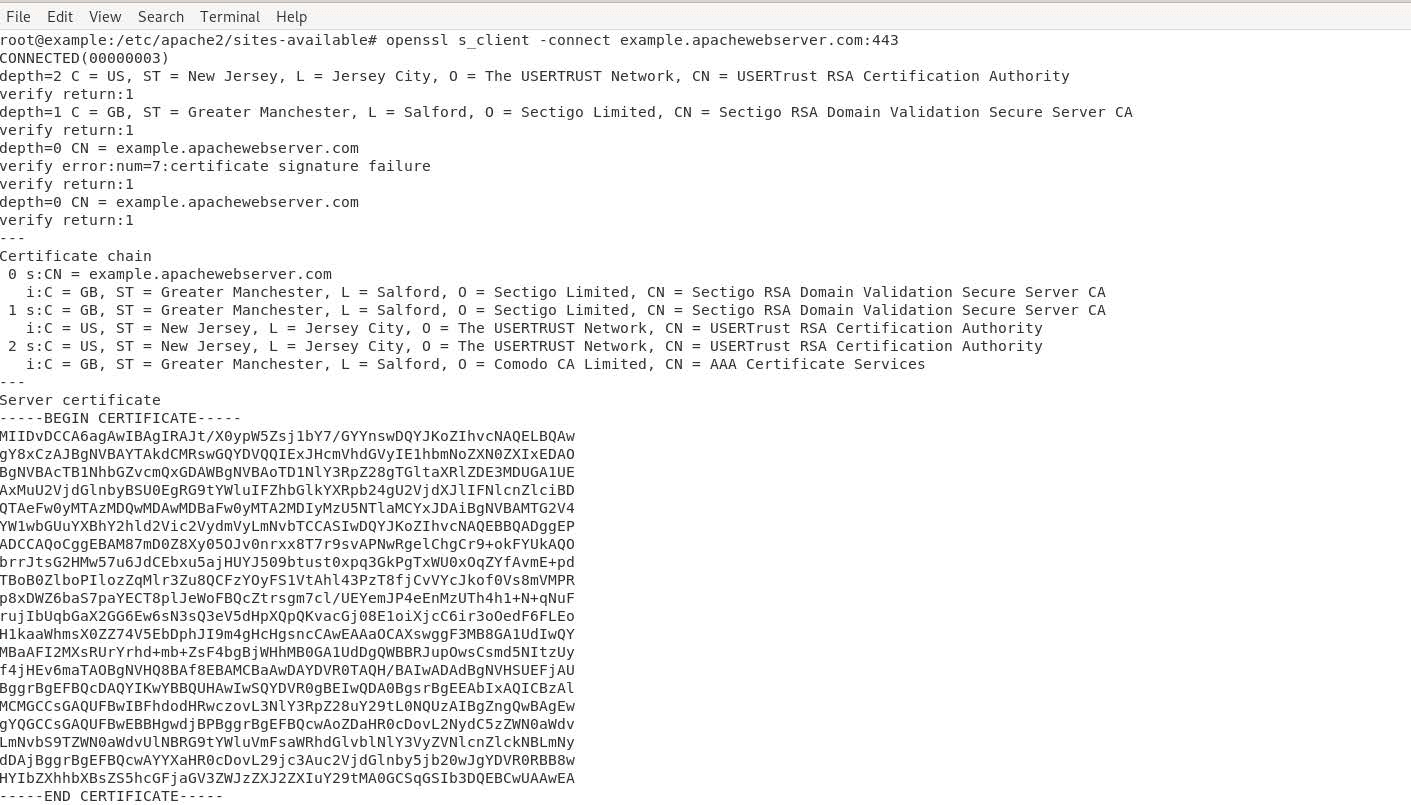
-
Navigate to
/etc/apache2/sites-available/and verify the SSL enablement details in your virtual host file.<IfModule mod_ssl.c> <VirtualHost *:443> ServerAdmin webmaster@localhost ServerName example.apachewebserver.com DocumentRoot /var/www/html ErrorLog ${APACHE_LOG_DIR}/error.log CustomLog ${APACHE_LOG_DIR}/access.log combined SSLCertificateFile /etc/letsencrypt/live/example.com/fullchain.pem SSLCertificateKeyFile /etc/letsencrypt/live/example.com/privkey.pem Include /etc/letsencrypt/options-ssl-apache.conf </VirtualHost> </IfModule>