Overview
Sectigo Connector for Akamai ("the connector") is a standalone solution created as a bash script to provide a secure automation layer for enrolling and managing Sectigo SSL/TLS certificates in Akamai Certificate Provisioning System (CPS).
The connector facilitates the automatic generation of a certificate signing request (CSR) with Akamai CPS and the enrollment, uploading, and management of certificates issued by a Sectigo private or public CA. It can obtain DV, OV, and EV SSL/TLS certificates, including SAN and wildcard certificates.
Akamai CPS supports the SHA-1 and SHA-256 hash functions (we recommend using SHA-256).
Once the Sectigo certificates are available on the page, they can be used to enable HTTPS communication for your secure content delivery network (CDN) applications. The connector also supports automatic certificate renewal before the certificate expiry or upon revocation.
The connector manages only the certificate enrollment with Sectigo SCM REST APIs and uploading the certificates to CPS. Deploying the provisioned certificates for your CDN applications is not in the scope of this solution.
Audience
This guide is intended for Akamai administrators and system administrators who have knowledge of IT security, cloud security, and are also familiar with Sectigo Certificate Manager (SCM).
Scope
This guide covers instructions on generating a CSR with Akamai, connecting to Sectigo SCM to provision certificates, and uploading certificates to Akamai CPS. Deploying the certificates for your CDN applications for SSL/TLS enablement is outside the scope of this guide.
Architecture
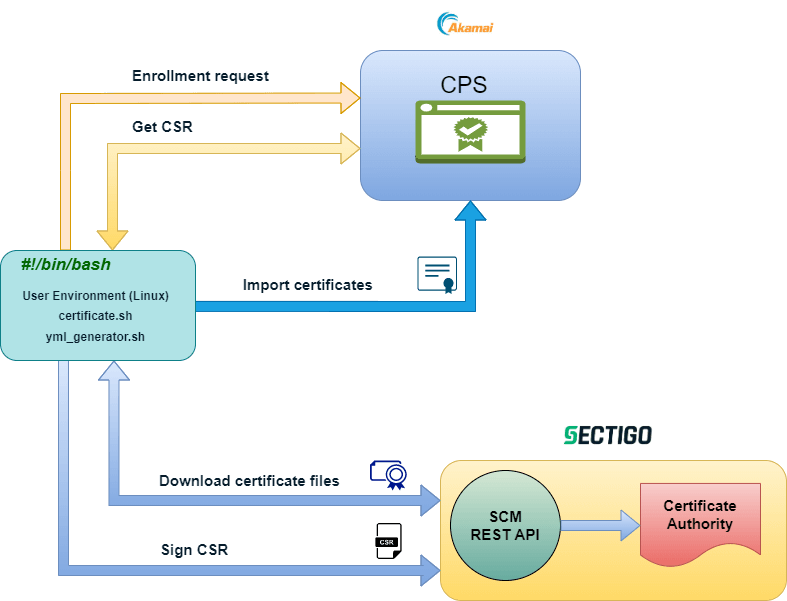
Execution workflow
-
Enrollment request for a third-party certificate is sent to Akamai CPS with information required for generating a CSR (if it’s a renewal operation for an existing certificate, the certificate revocation and expiration status is checked).
-
Akamai generates a CSR for the certificate, and SectigoAkamaiCM downloads the CSR.
-
The CSR is sent to the Sectigo CA.
-
The enrolled certificate and certificate chain files are downloaded from the CA.
-
The certificate files are uploaded to Akamai CPS.
Package contents
The following image shows the package structure.
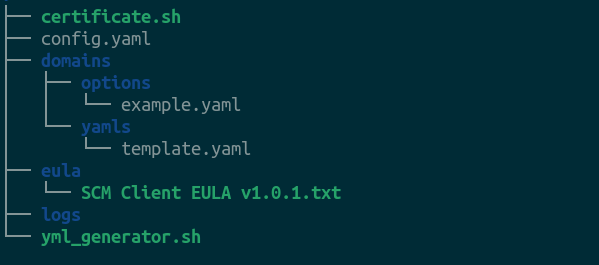
The package contains the following components:
-
certificate.sh: This script implements certificate-related actions (enrolling or renewing certificates, retrieving certificate details, creating logs, and more).
-
config.yaml: This configuration file contains the Sectigo API credentials.
-
domains: This directory contains configuration and template files.
-
options: This directory contains the configuration files for certificates.
-
example.yaml: This sample certificate profile file contains information about the certificate type, contact details of the certificate requester, CSR information, and more. You can have multiple copies of this file with your preferred naming convention (for example,
<domain_name>.yaml), one file for each certificate to be provisioned. Theyml_generator.shscript uses the values from this file to prepare the./domains/yamls/<domain_name>.yamlcertificate profile file.
-
-
yamls: This directory contains the
template.yamlfile that is used by thecertificate.shscript to prepare the./domains/yamls/<domain_name>.yamlcertificate profile file.-
template.yaml: The
yml_generator.shscript replaces values in this template file with values collected from the./domains/options/<domain_name>.yamlfile, then the script copies the contents of this file to a new./domains/yamls/<domain_name>.yamlfile.
-
-
-
eula: This directory contains the SCM EULA agreement file.
-
SCM Client EULA v1.0.1.txt: The EULA agreement. You need to accept it when running the
certificate.shscript for the first time.
-
-
logs: This directory contains the
<domain_name>.logfiles created by thecertificate.shscript. -
yml_generator.sh: This script creates the
./domains/yamls/<domain_name>.yamlcertificate profile file.