Overview
Sectigo Connector for Palo Alto Firewall ("the connector") is a certificate management solution developed to automate the enrollment and management of SSL/TLS certificates for Palo Alto VM-Series virtual next-generation firewall (including Palo Alto Panorama) to secure communication between the external clients and applications behind the firewall.
The certificate lifecycle management is handled by Sectigo SDK for Python which communicates with the Sectigo backend server through the SCM enrollment API to request and renew SSL/TLS certificates, and import them into the certificate management area of Palo Alto Firewall using the PAN-OS REST API.
The connector can obtain the following types of SSL/TLS certificates:
-
Domain Validation (DV) certificates
-
Organization Validation (OV) certificates
-
Extended Validation (EV) certificates
The following key types are supported: RSA (2048-bit, 3072-bit, and 4096-bit) and ECDSA (P256r1, P384r1, and P521).
Audience
This document is intended for IT administrators and network administrators who manage Palo Alto virtualized firewalls.
Scope
This guide contains instructions for enrolling and managing Sectigo certificates on Palo Alto virtualized firewalls. It does not cover configuration of firewalls.
Architecture
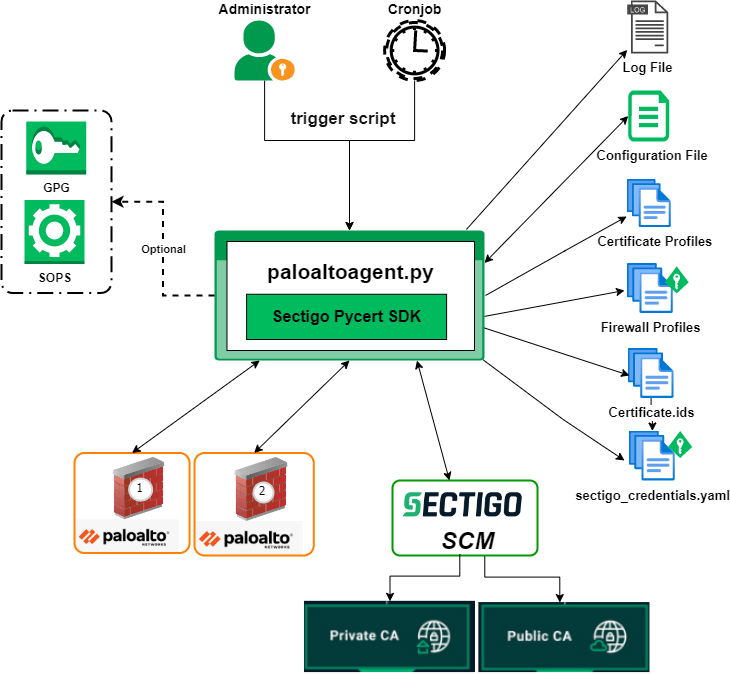
The connector is developed using Sectigo Certificate Manager (SCM) SDK for Python. The SDK uses the SCM REST API to securely authenticate and communicate with the Sectigo backend for certificate management.
Package contents
The package contains the following components:
-
paloaltofw: This folder and its subfolders contain the connector and configuration files
-
paloaltoagent.py: The connector as an executable file
-
config.yaml: This file stores the configuration for SCM, logging, and encryption
-
profiles_sample: This folder contains sample configuration files for a certificate profile, firewall profile, and SCM credentials
-
certificate.yaml: A sample configuration file for a certificate profile
-
fw_paloalto_config.yaml: A sample configuration file for a firewall profile
-
sectigo_credentials.yaml: This file stores SCM credentials
-
-
-
SCM Client EULA v1.0.1.txt: The EULA agreement. You need to accept it when running the connector for the first time.
-
requirements.txt: This file contains a list of Python dependencies
Execution workflow
The connector is triggered manually or automatically through a cronjob. You specify which operation will be performed by the connector and, optionally, define the certificate profile name when the target is a specific certificate profile. The available operations include enrollment, renewal, encryption, and decryption.
The connector performs the following actions:
-
It loads its configuration from the
config.yamlfile. The path to the config file is stored in thesectigo_pycert_configenvironment variable. Alternatively, the connector looks for the file in the relative path ofpaloaltoagent.py. The connector reads information from the config file, such as the SCM API URL, the log level, the path for saving the log file and its name, and the path to the certificate and firewall profiles. -
It reads the certificates and firewall profile files. Each certificate profile describes a unique certificate that can be DV, OV, or EV. The certificate profile file contains all the information related to the certificate, such as domains, SANs, key type and size, and the target firewall name. The firewall profile contains information related to the Palo Alto firewall instance, such as the API key, URL or IP address, admin name, and commit description. You can encrypt these credentials using GPG.
-
It sends a request to Palo Alto to check whether a certificate named as the certificate profile already exists. If the certificate doesn’t exist, or is expired or revoked, the connector calls the Palo Alto API to generate a CSR with the certificate information. Palo Alto creates an asymmetric key pair with the key type and size defined in the certificate profile, then creates a CSR using the public key and signs it with the private key. The private key isn’t exposed to the outside world—it is kept private inside the Palo Alto firewall.
-
It downloads the CSR and submits it to the Sectigo CA (Public or Private CA) which issues an SSL/TLS certificate based on the information in the CSR. The connector downloads the certificate chain.
-
It saves the certificate ID in Base64 format to a file with the
.idsextension, imports the downloaded certificate chain into Palo Alto, and commits the changes. -
It writes the main events that occur during enrollment or renewal of a certificate into the log file.