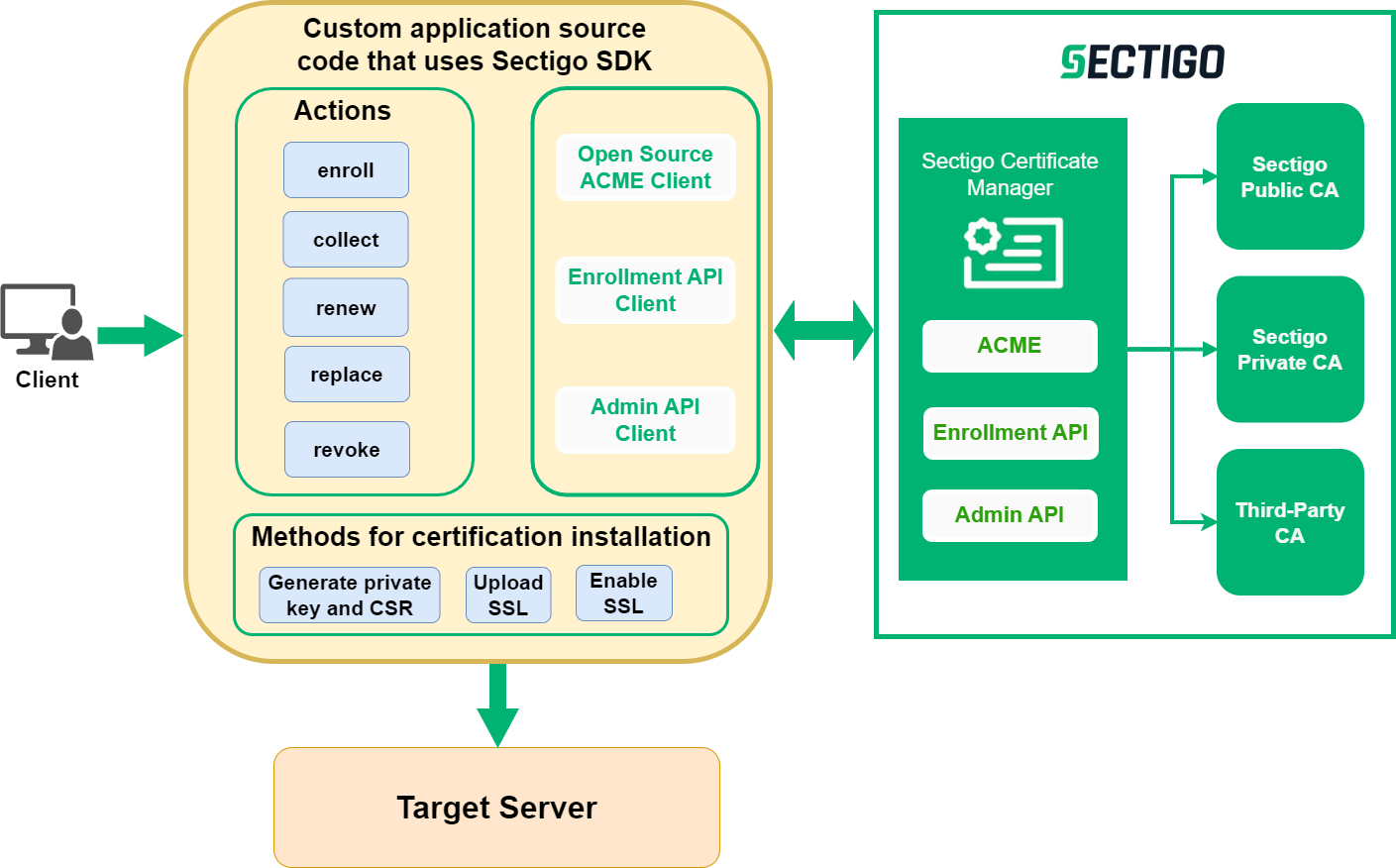
Overview
The Sectigo Client SDK v2.0 ("the SDK") is a client library that lets you interact with Sectigo Certificate Manager (SCM) to perform enrollment, renewal, and replacement of SSL/TLS certificates issued by Sectigo or a third-party CA. Both public and private CAs are supported. The SDK supports the Enrollment API, Admin API, and ACME protocol based on the SCM endpoints.
The SDK makes it easy for developers to create custom solutions with embedded certificate lifecycle management capabilities. It provides an easy-to-use interface for performing common API operations such as sending HTTP requests and handling responses.
Supported certificate types
The following table shows which certificate types are supported by each CA.
| CA Type | Private SSL | DV SSL | OV SSL | EV SSL |
|---|---|---|---|---|
Sectigo |
Yes |
Yes |
Yes |
Yes |
AWS Private CA |
Yes |
No |
No |
No |
DigiCert |
No |
No |
Yes |
Yes |
Entrust |
No |
No |
Yes |
Yes |
GCP CA Service |
Yes |
No |
No |
No |
Microsoft CA |
Yes |
No |
No |
No |
Supported certificate types:
-
Domain Validation (DV): Single-domain, multi-domain, and wildcard certificates issued by Sectigo
-
Organization Validation (OV): Single-domain, multi-domain, and wildcard certificates issued by Sectigo or a third-party CA
-
Extended Validation (EV): Single-domain and multi-domain certificates issued by Sectigo or a third-party CA
-
Private SSL: Private SSL certificates issued by Sectigo or a third-party CA for internal use
Supported CAs:
-
Public CA: Sectigo, Entrust, and Digicert
-
Private CA: Sectigo, Microsoft CA, AWS Private CA, and Google Cloud CA Service
Supported key types:
-
RSA: 2048-bit, 3072-bit, and 4096-bit
-
ECDSA: P256r1 and P384r1
Best practices
These are best practices for using the SDK:
-
The SDK is intended to be used as a library in other applications, not as a standalone application.
-
Avoid hardcoding API credentials in your application—use the SDK configuration options instead. The SDK can retrieve configuration details from a configuration file or configuration struct.
-
If you have credentials for different applications in your environment, don’t store all credentials together. Keeping credentials separate enables easier management of credentials and reduces the impact scope in case of a security breach.
Audience
This guide is intended for product managers, development managers, software developers, and integration engineers who want to learn how to use the SDK to automate certificate lifecycle management.
Scope
This guide covers details on the SDK implementation to help Sectigo developers and customers create third-party integrations for managing the lifecycle of SSL/TLS certificates.