Overview
Sectigo Connector for HAProxy ("the connector") is a secure automation solution created as a binary executable file for enrolling and managing SSL/TLS certificates issued by Sectigo or a third-party certificate authority (CA) to support encrypted communication between external clients and HAProxy load balancers.
The connector lets security administrators automate the certificate lifecycle management and enable SSL on HAProxy. The provisioned certificates are uploaded to the certificate area of HAProxy and automatically attached to the load balancers.
The following certificate types are supported:
-
Domain Validation (DV): Single-domain, multi-domain, and wildcard certificates issued by Sectigo
-
Organization Validation (OV): Single-domain, multi-domain, and wildcard certificates issued by a Sectigo or third-party CA
-
Extended Validation (EV): Single-domain and multi-domain certificates issued by a Sectigo or third-party CA
-
Private SSL: Private SSL certificates issued by a Sectigo or third-party CA for internal use
The following CAs are supported:
-
Public CA: Sectigo, Entrust, and Digicert
-
Private CA: Sectigo, Microsoft CA, AWS Private CA, and Google Cloud CA Service
The following key types are supported: RSA (2048-bit, 3072-bit, and 4096-bit) and ECDSA (P256r1 and P384r1).
Audience
This guide is intended for HAProxy administrators and system administrators who have knowledge of IT security, cloud security, and are also familiar with Sectigo Certificate Manager (SCM).
Scope
This guide covers instructions on connecting to the Sectigo ACME servers to enroll or renew certificates, and then attach the certificates to load balancers.
Architecture
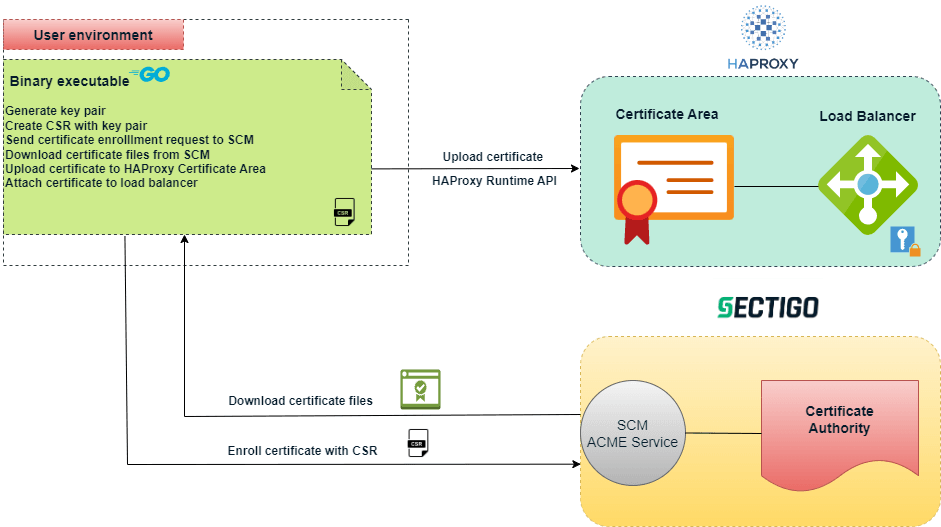
Execution workflow
During execution, the connector does the following:
-
Reads the certificate enrollment information from the certificate profile file.
-
Generates a key pair and creates a certificate signing request (CSR).
-
Sends the CSR with an enrollment request to SCM.
-
Retrieves the certificate chain in PEM format from SCM.
-
Uploads the certificate chain and private key to the HAProxy certificate area.
-
Associates the certificate with the load balancer.