Overview
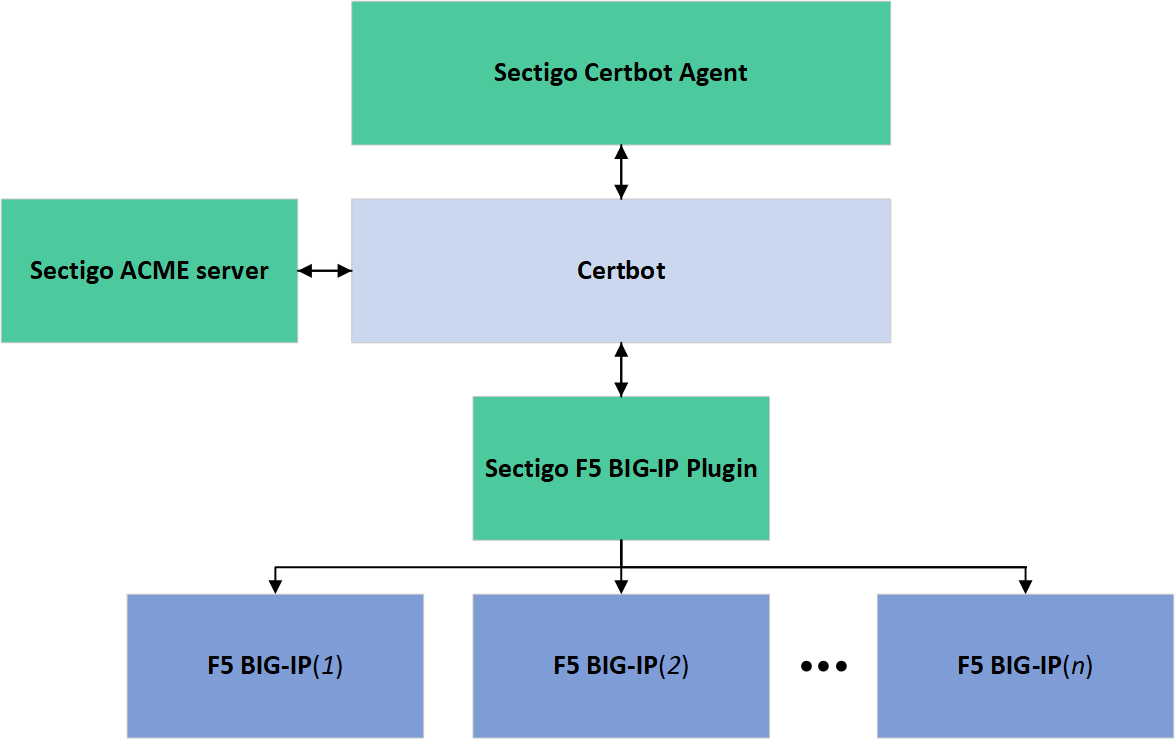
Sectigo Connector for F5 BIG-IP ("the connector") is an automation layer developed around the open source Certbot BIG-IP plugin. The connector uses the Certbot BIG-IP plugin to support more features, in addition to the default features of the plugin. The default plugin comes with only certificate enrollment capabilities. Sectigo adds another layer of features on the default plugin to automate the complete SSL certificate management for the HTTP virtual servers on an F5 BIG-IP appliance.
The certificate lifecycle management is handled by the connector that invokes the Certbot plugin to communicate with the Sectigo ACME server to request, renew, or revoke SSL/TLS certificates, install them on the F5 appliances, and enable SSL features on the virtual servers.
Certbot BIG-IP plugin default supported features
-
Enrolling certificates for a standalone F5 appliance or and an HA group (active/standalone, active/standby, active/active)
The connector doesn’t control config sync for an HA group—an SSL/TLS certificate is deployed to one of the devices in a device group, and the BIG-IP system is responsible for propagating configuration changes to all devices in the group. -
Creating a client SSL profile based on the parent profile and attaching the certificate, private key, and CA chain to the virtual server
Sectigo F5 Connector v2.0 supported features
-
Payment Card Industry (PCI) compliance—private keys are generated on BIG-IP with password protection
-
Support for a custom parent profile
-
Automatic SSL enablement on the virtual servers of BIG-IP using the new client SSL profile(s)
-
Auto-renewal and key management of SSL/TLS certificates on multiple BIG-IP appliances
-
Support for both RSA and ECDSA key types (currently supports only the curve secp256r1)
-
Support for multi-domain certificates and wildcard certificates
-
Custom log levels
-
The ability to enable certificate management on specific virtual servers
-
Support for Server Name Identification (SNI)
Audience
This guide is intended for IT administrators and network administrators who manage BIG-IP appliances for an organization.
Scope
This guide contains instructions for enrolling and managing Sectigo certificates on BIG-IP appliances. Configuration of appliances is out of the scope of this guide.
Execution workflow
The connector conceals the complexity of performing private key generation on the BIG-IP appliance, CSR creation, certificate issuance, installing the server certificate and CA chain to multiple remote BIG-IP appliances and enabling SSL on the virtual servers.
The version 2.0 of the connector is PCI compliant, which means that the private key is protected using a password and generated on the BIG-IP appliance. The private key is never exposed to the connector machine or outside BIG-IP during the TLS handshake.
To do this, the connector provides a command-line interface ./start_acme.py that connects to BIG-IP via the Certbot BIG-IP plugin and BIG-IP REST API.
The connector is packaged with the Certbot client to authenticate to Sectigo ACME server and request a new certificate from the Sectigo ACME server as per the YAML configuration file, automatically install the certificate on the BIG-IP appliances, and enable a secure connection (SSL) on the virtual servers.
Once the script is started, the connector performs the following:
-
Reads every YAML configuration file from the
/etc/sectigodirectory -
Connects to BIG-IP using the IP address and credentials provided in the YAML file or in a separate credential file
-
Checks whether a certificate exists in the Common Name provided in the YAML file
-
Generates a password protected private and public key pair based on the key type/size provided in the YAML file. The connector uses a random password generator with software entropy to generate the password. Once a custom client SSL profile is created with the key, certificate, and password, the password is erased from memory. The password is not stored on disk, so it cannot be retrieved to export the private key from BIG-IP.
-
Generates a certificate signing request (CSR) on BIG-IP
-
Downloads the CSR to the Linux client machine
-
Connects to the Sectigo ACME server using the credentials from the
envfile -
Registers the connector with the Sectigo ACME server
-
Submits the CSR to request a new certificate
-
Uploads the CA chain and new server certificate to BIG-IP
-
Creates a custom client SSL profile using the certificate, private key, and password
-
Enables SSL on the virtual servers using the configured client SSL profile