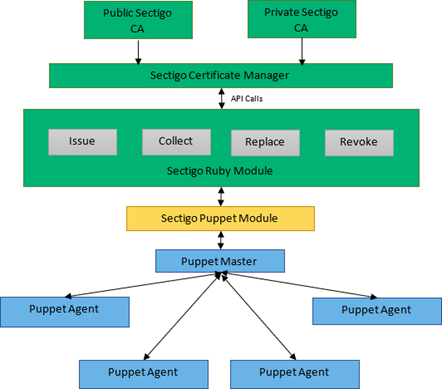
Overview
The Sectigo Puppet integration provides a solution for the enrollment, collection, renewal, replacement, and revocation of SSL/TLS and client (S/MIME) certificates issued by the Sectigo Certificate Manager (SCM).
The integration is distributed as a Puppet module featuring the following:
-
RSA 2048, 3072, and 4096-bit private key generation
-
Certificate signing request (CSR)
-
Enrollment, collection, renewal, replacement, and revocation of certificates issued by SCM
The integration supports the generation of new SSL and client certificates and detection of existing certificates stored in a location accessible to the module at runtime. The integration also checks the validity of existing certificates and allows the issuance of replacement certificates as required. You can request different types of SSL and client certificates by supplying appropriate configuration options.
| The types of SSL and client certificates available to you are based on your account configuration. |
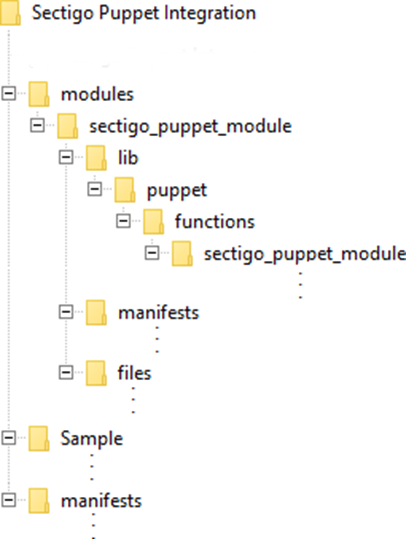
Package contents
The Sectigo Puppet integration package contains the following:
-
modules:
-
sectigo_puppet_module:
-
files: Contains static files
-
index.html: Sample dashboard
-
server_httpd.conf: Sample HTTPD server configuration
-
server_nginx.conf: Sample NGINX server configuration
-
ssl_redirect.conf: Sample server redirect HTTP to HTTPS
-
-
lib/puppet/functions/sectigo_puppet_module:
-
constants.rb: Constants file for the SCM API library
-
rbcert.rb: Ruby library for connecting with the SCM API
-
helper.rb: Common function file
-
sectigo_puppet_module.rb: Main Ruby file designed for Puppet
-
-
manifest
-
httpd.pp: Sample HTTPD configuration
-
init.pp: Manifest files that calls Ruby
-
nginx.pp: Sample NGINX configuration
-
-
-
-
manifests:
-
site.pp: The catalog for the Puppet server. This file contains a configuration that can be used to generate certificate on servers and that can be used to move existing certificates from master to agent nodes.
-
-
Sample:
-
config_sample_account.json: Sample Facter configuration with SCM account-related parameters
-
config_sample_issue_ssl.json or config_sample_issue_client.json: Sample Facter configuration with parameters that are used for SSL or client certificate issuance.
-
config_sample_node_ssl.json: Sample Facter configuration with parameters that are used for moving SSL certificates onto a Puppet node.
-
fileserver.conf: Sample configuration file for the Puppet file server
-
run.sh: A shell script that can be used in a cronjob to automate the execution of the module
-