Overview
Sectigo Connector for IIS ("the connector") is a solution for automating the enrollement and installation of Sectigo certificates on the IIS web server with Automatic Certificate Management Environment (ACME). The connector is based on the win-acme client.
The ACME protocol provides the ability to automatically enroll and install a new SSL/TLS certificate on a web server, renew a certificate nearing expiration, and revoke the certificate in the event of key compromise or web service discontinuation. This guide provides instructions on manual and automatic enrollment of SSL/TLS web server certificates using the ACME client implementation called win-acme.
ACME protocol
ACME is a protocol for automating certificate lifecycle management communications between certificate authorities (CAs) and a company’s web servers, email systems, user devices, and any other place where public key infrastructure (PKI) certificates are used. The ACME protocol has no licensing fees and requires very little time for IT teams to configure and execute their certificate management automation, making it an increasingly adopted component of enterprise security.
The Internet Security Research Group (ISRG) originally designed the ACME protocol for its own certificate service and published the protocol as a full-fledged Internet Standard in RFC 8555 by its own chartered IETF working group. ACME v2 is the current version of the protocol, published in March 2018.
The basis for PKI certificate issuance is that certificate authorities, like Sectigo, are trusted to authenticate that a certificate user legitimately represents the identities and domain name(s) associated with the PKI certificate. The process for exchanging information necessary for the CA to perform that authentication and issue certificates, and for the user to then deploy the issued certificates, is automated using the ACME protocol, rather than communicating this information manually. In addition to the certificate issuance process, the protocol also enables other certificate lifecycle management use cases like certificate revocation and renewal, using simple JSON-formatted messages over encrypted HTTPS communications.
ACME service architecture
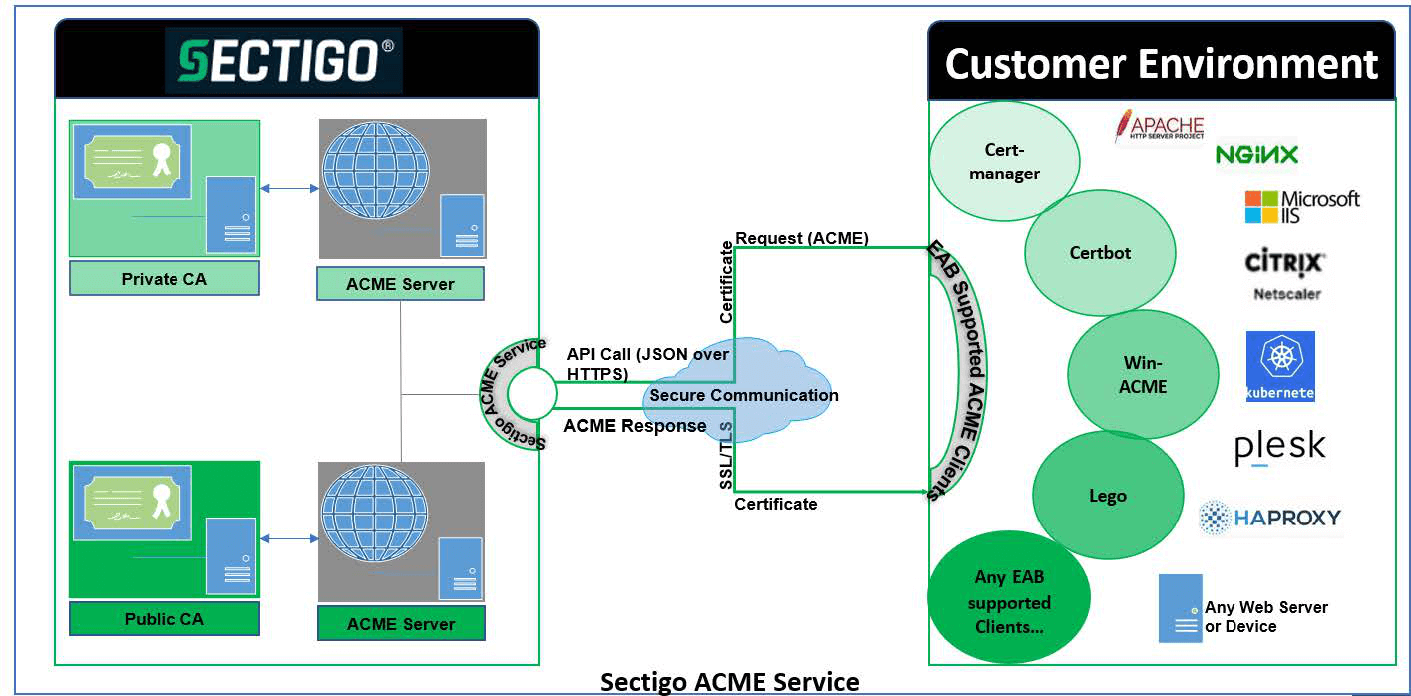
ACME clients communicate with Sectigo ACME servers to request and manage certificates through ACME enrollment endpoints. ACME enrollment endpoints are HTTPS-based URLs where the ACME server listens for the request from the ACME client with supported parameters. The client sends a request for certificate management actions using a set of JavaScript Object Notation (JSON) messages carried over HTTPS.
Certificate management using ACME is similar to any other protocols, like PKIX-CMP or SCEP, where a user account is created on the CA side; the user requests a certificate using the shared secrets (or authorization codes), and provides proof of possession of private key and additional domain validation for DV certificates, in order for the CA to issue the requested certificate.
Sectigo serves certificates to the customer through the following categories of ACME endpoints within public ACME and private ACME:
-
DV certificate endpoint: Issues Domain Validated certificates. For more information, see Domain control validation methods.
-
OV certificate endpoint: Issues Organization Validated certificates. For more information, see Organization Validated Certificates.
-
EV certificate endpoint: Issues Extended Validation Certificates. For more information, see EV Certificates.
The types of CAs:
Public ACME: Connects to the public ACME service that is connected to the public CA to enroll and manage SSL certificates.
Private ACME: Connects to the private ACME service that is connected to a private CA and uses private trust level certificate profiles for enrolling and managing SSL certificates.
| The endpoints available depend on the features that have been enabled for your account. |
Automated certificate management with the Sectigo ACME service
There are four major steps to complete for successful enrollment with the Sectigo ACME server for server certificates:
-
ACME account creation (pre-registration on SCM is required).
-
Domain validation and delegation.
-
Domain validation is not required for private ACME (connecting to private CA).
-
Domain validation for public ACME (connecting to public CA) has two cases:
-
Domain validated in SCM—no challenges are issued via ACME.
-
Domain not validated in SCM—ACME will issue challenges to validate the requested domains.
-
-
-
ACME client registration using External Account Binding identifier (key ID) and authorization code (HMAC key).
-
Certificate signing request (CSR) submission and certificate issuance.
Deployment model with domain validation in SCM
-
Customer creates an account on the ACME server through SCM to bind the SCM account with the ACME account.
-
This creates External Account Binding (authorization code) values for the ACME account for a specific endpoint.
-
-
System administrators send these EAB values (key ID and HMAC key) along with other certificate related information to a specific enrollment endpoint (the ACME server) through ACME clients.
-
ACME server checks the EAB values, links the accounts, and then deletes the EAB on the server side so that it cannot be reused on a different server.
-
This restricts the use of the same EAB keys on different servers with different accounts.
-
-
All future ACME requests, such as enrolling or renewing certificates, are done using the registered key pair from the web server.