Overview
Sectigo Connector for Kemp ("the connector") is a secure automation solution for enrolling and managing Sectigo SSL/TLS certificates to support encrypted communication between clients and Kemp LoadMaster load balancers. Certificates are automatically attached to the virtual services.
The provisioned certificates are uploaded to the certificate area of LoadMaster using the LoadMaster RESTful API.
The connector can provision Domain Validation (DV), Organization Validation (OV), and Extended Validation (EV) SSL/TLS certificates, including SAN and wildcard certificates, for Hardware, Virtual, Cloud, or Free LoadMaster. It works with both public and private CAs. The following key types are supported: RSA (2048-bit and 4096-bit) and ECDSA (256-bit and 384-bit).
Audience
This guide is intended for security administrators who manage Kemp LoadMaster for an organization and are responsible for automating the certificate lifecycle to enable secure communication between clients and load balancers.
Scope
This guide covers instructions for enrolling Sectigo server certificates and enabling SSL on LoadMaster virtual services.
Architecture
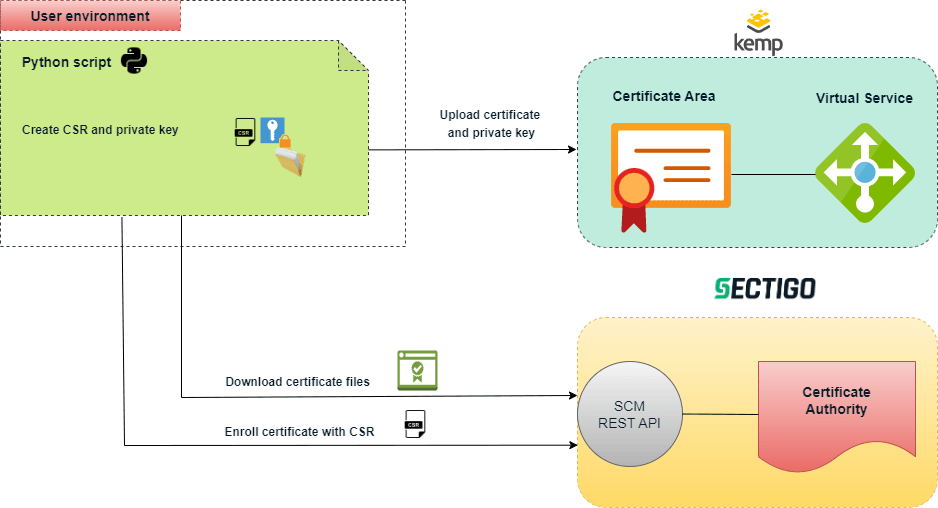
Execution workflow
During execution, the script does the following:
-
Reads the certificate enrollment information from the certificate profile file.
-
Generates a key pair and creates a certificate signing request (CSR).
-
Sends the CSR with an enrollment request to SCM.
-
Retrieves the certificate chain in PEM format from SCM.
-
Uploads the certificate chain and private key to the LoadMaster’s certificate area using the RESTful API.
-
Installs the certificate to the virtual service.
Package contents
The package contains the following components:
-
config: This directory contains configuration files.
-
kemp_profile_1.yaml: The Kemp profile file
-
cert_profile_1.yaml: The certificate profile file
-
config.yaml: The config file
-
sectigo_credentials.yaml: The SCM credentials file
-
-
main.py: The connector as an executable file
-
.py: Python source files in their respective directories
-
requirements.txt: This file contains a list of Python dependencies
-
SCM Client EULA v1.0.1.txt: The EULA agreement