Overview
Sectigo Connector for AWS ("the connector") is an AWS serverless solution created using a Lambda function which provides a secure automation layer for enrolling Sectigo SSL/TLS certificates using the ACME protocol, and importing the Sectigo certificates into AWS Certificate Manager (ACM). The connector can be deployed for one or more AWS accounts.
Once the Sectigo certificates are available in ACM, they can be used to enable secure communication with AWS load balancers, CloudFront, or any other Amazon Web Services over HTTPS. The connector supports automatic certificate renewal before the certificate expiry date and upon revocation.
Audience
This guide is intended for AWS administrators and system administrators who have knowledge of IT security, cloud security, and are also familiar with Sectigo Certificate Manager (SCM).
Scope
This guide covers instructions for connecting to the Sectigo ACME servers, enrolling, and uploading certificates to ACM. Attaching the certificates to load balancers for SSL/TLS enablement is outside the scope of this guide. We assume that you will associate an SSL/TLS certificate with a target load balancer yourself. Example script for Terraform is provided for your reference.
Architecture
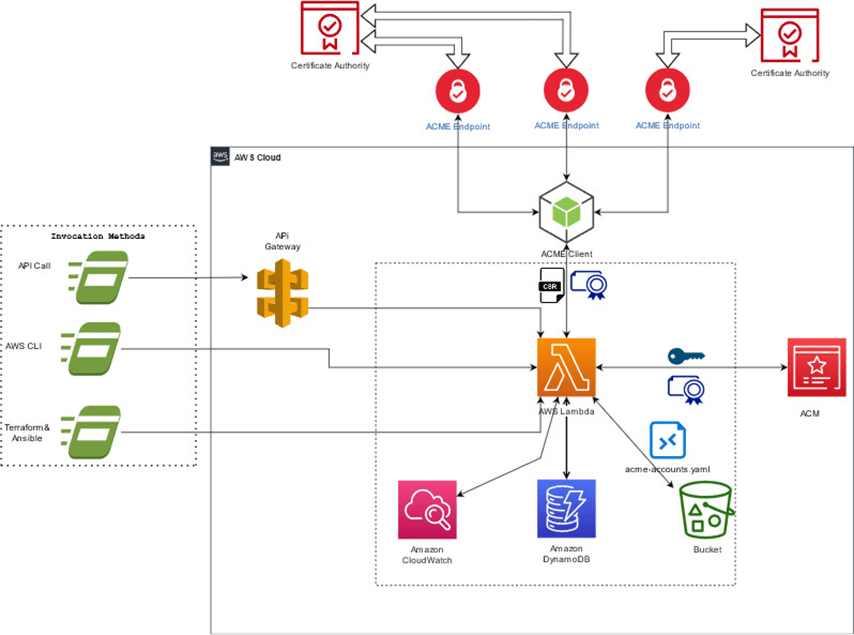
The execution is controlled using the AWS resource policies. Only the specified principals (typically an IAM user or role) can invoke the Lambda function.
Users of the connector are responsible for configuring it with information about each ACME account that will be used. Each account is identified by an alias. Some configuration information, such as External Account Binding (EAB) parameters, can be collected from SCM. When enrolling certificates using the connector, users control which ACME account settings to use for enrollment, by passing the ACME account alias as a parameter.
| Since the connector is using Certbot as the ACME client, the current iteration of the product only allows EAB information corresponding to one ACME account to be used for each ACME endpoint. To control other parameters (for example, the key size), you can define multiple aliases for the same ACME account. |
Since certificates in ACM are regional resources, the connector is region specific. When you have multiple AWS regions, the script should be run separately for each region.
Deployment overview
The SectigoAWS Lambda function is deployed to AWS with the Terraform CLI.
The AWS CLI is used to invoke the Lambda function.
AWS CLI commands are also used in the install.sh and destroy.sh scripts.
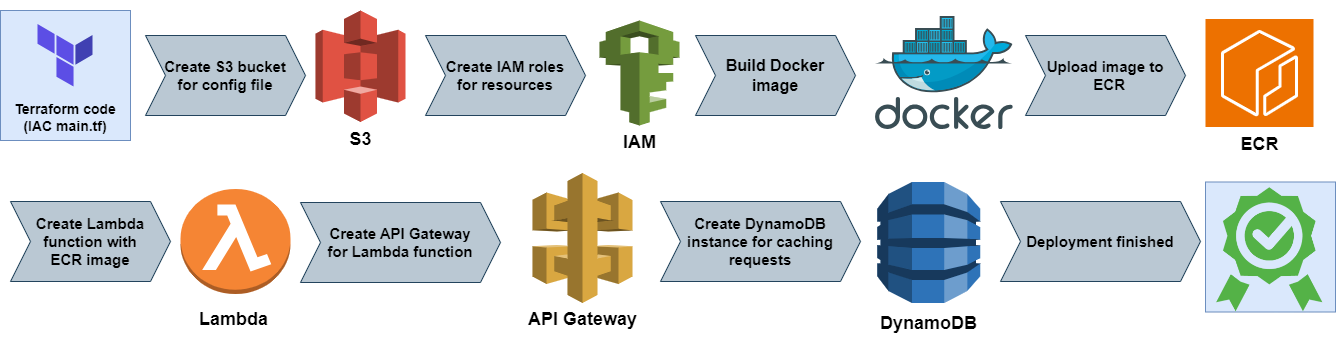
Modules
The connector uses nested modules, one module per AWS service:
-
s3: Securely stores the
acme-account.yamlfile -
iam: IAM roles and policies for interaction between other resources
-
lambda: The Lambda function that provides the core enroll and renew actions
-
api-gateway: Allows the Lambda function to be invoked via REST API
-
dynamodb: Keeps track of Lambda request instances
AWS resources
| Resource Name | Description |
|---|---|
|
IAM policy for access to S3 bucket from Lambda |
|
Creates CloudWatch log group for Lambda |
|
IAM policy resource for creating and accessing Cloudwatch logs for Lambda |
|
Creates API key ( |
|
S3 bucket for the |
|
IAM role for the Lambda function |
|
Attaches S3 Lambda policy to Lambda role |
|
Attaches Lambda log policy to Lambda role |
|
Creates Lambda function |
|
Creates REST API Gateway for Lambda |
|
Permission for invoking Lambda via API Gateway |
|
Deploys |
|
Creates API stage |
|
Usage plan for API Gateway |
|
Binds API key ( |
|
S3 bucket public access restrictions |
|
DynamoDB table for storing requests |
IAM policies
| Service | Action | Resource |
|---|---|---|
ACM |
Add tags to certificate |
All certificates |
ACM |
List tags for certificate |
All certificates |
ACM |
Describe certificate |
All certificates |
ACM |
Get certificate |
All certificates |
ACM |
List certificates |
All certificates |
ACM |
Import certificate |
All certificates |
S3 |
Get object |
The bucket for account |
S3 |
Get object version |
The bucket for account |
Lambda |
Invoke function |
Function itself |
Lambda |
Invoke function |
API Gateway |
DynamoDB |
All actions |
SectigoAWSCM table |
Logs |
Create log group |
arn:aws:logs:*:*:* |
Logs |
Create log stream |
arn:aws:logs:*:*:* |
Logs |
Put log events |
arn:aws:logs:*:*:* |