Overview
Sectigo Connector for Citrix ("the connector") is a certificate management solution developed to automate the enrollment and management of SSL/TLS certificates, securing communication between the external clients and the Citrix load balancer. The connector supports the following servers, configured on Citrix v13.0 or later:
-
load balancing
-
gateway
-
content switching
-
authentication
The certificate lifecycle management is handled by Sectigo SDK for Python which communicates with the Sectigo backend server through the Sectigo Certificate Management (SCM) enrollment API to request, renew, or replace SSL/TLS certificates, and import them to the Citrix certificate store using the NITRO REST API.
The following key types are supported:
-
RSA (2048-bit, 3072-bit, and 4096-bit)
-
ECDSA (P256r1 and P384r1).
Audience
This guide is intended for IT administrators and network administrators who manage Citrix appliances.
Scope
This guide contains instructions for enrolling and managing Sectigo certificates on Citrix appliances. It does not cover configuration of Citrix appliances.
It’s assumed that a Citrix environment with either a physical Citrix appliance or Citrix VPX (virtual server) already exists and is configured with virtual server(s) where you want to install SSL/TLS certificates.
Architecture
The connector is developed using Sectigo Certificate Manager (SCM) SDK for Python. The SDK uses the SCM REST API to securely authenticate and communicate with the Sectigo backend for certificate management.
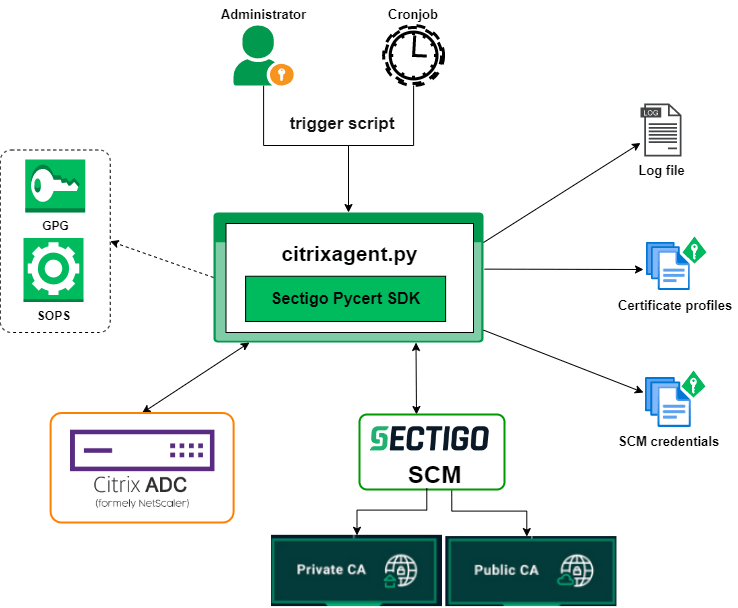
Package contents
The package contains the following components:
-
citrixagent.py: The entry point of the connector.
-
example_cert_config.yaml: A sample certificate profile file.
-
scm.yaml: This file contains the SCM credentials.
-
README.md: This file contains instructions on using the connector.
-
requirements.txt: This file contains a list of Python dependencies.
-
LICENSE.txt: The EULA agreement. You need to accept it when running the connector for the first time.
Execution workflow
-
An authorized administrator downloads and installs the connector on a secure system which has access to the Internet and Citrix appliance to enroll and manage SSL/TLS certificates. The connector can be executed either manually by the admin or automatically using a cronjob.
-
The connector reads the following files:
-
The configuration file which contains the SCM connection details
-
The certificate profile file which contains the details on the Citrix appliance and certificate attributes details
-
-
Using the certificate profile configurations, the connector connects to the Citrix appliance to generate an asymmetric key pair and a CSR, and downloads the CSR to the local connector’s system.
-
The CSR is uploaded to the Sectigo backend for certificate enrollment after a successful client authentication.
-
The enrolled certificate is imported to the Citrix appliance to enable SSL on the virtual server.
| A single certificate profile file can have the details of more than one virtual server—in this case, all the virtual servers will receive the same SSL/TLS certificate. To enroll unique certificates for each virtual server on an appliance, create individual YAML files for each virtual server. We recommend that you maintain individual YAML files for each virtual server to prevent key reuse. |