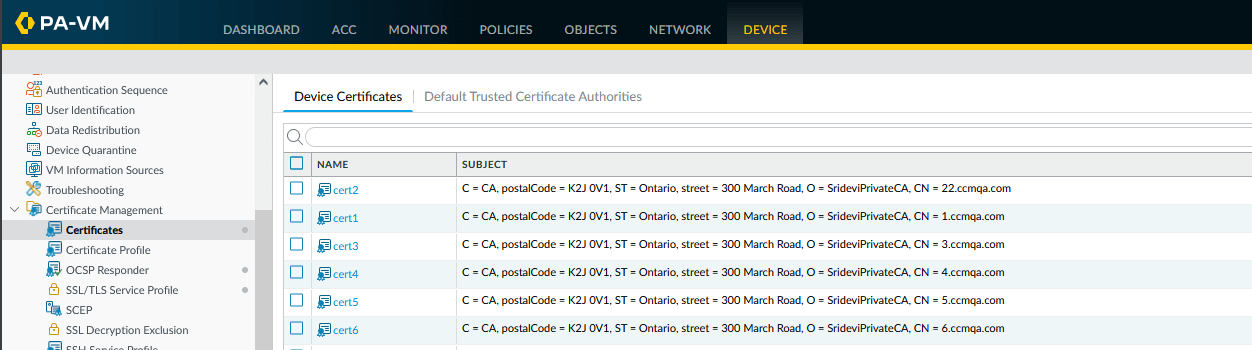
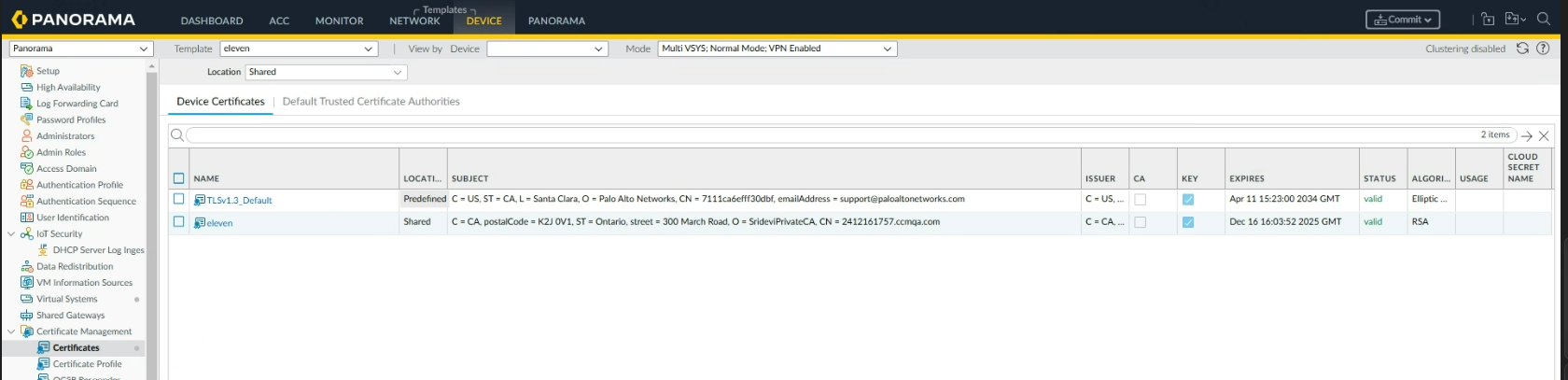
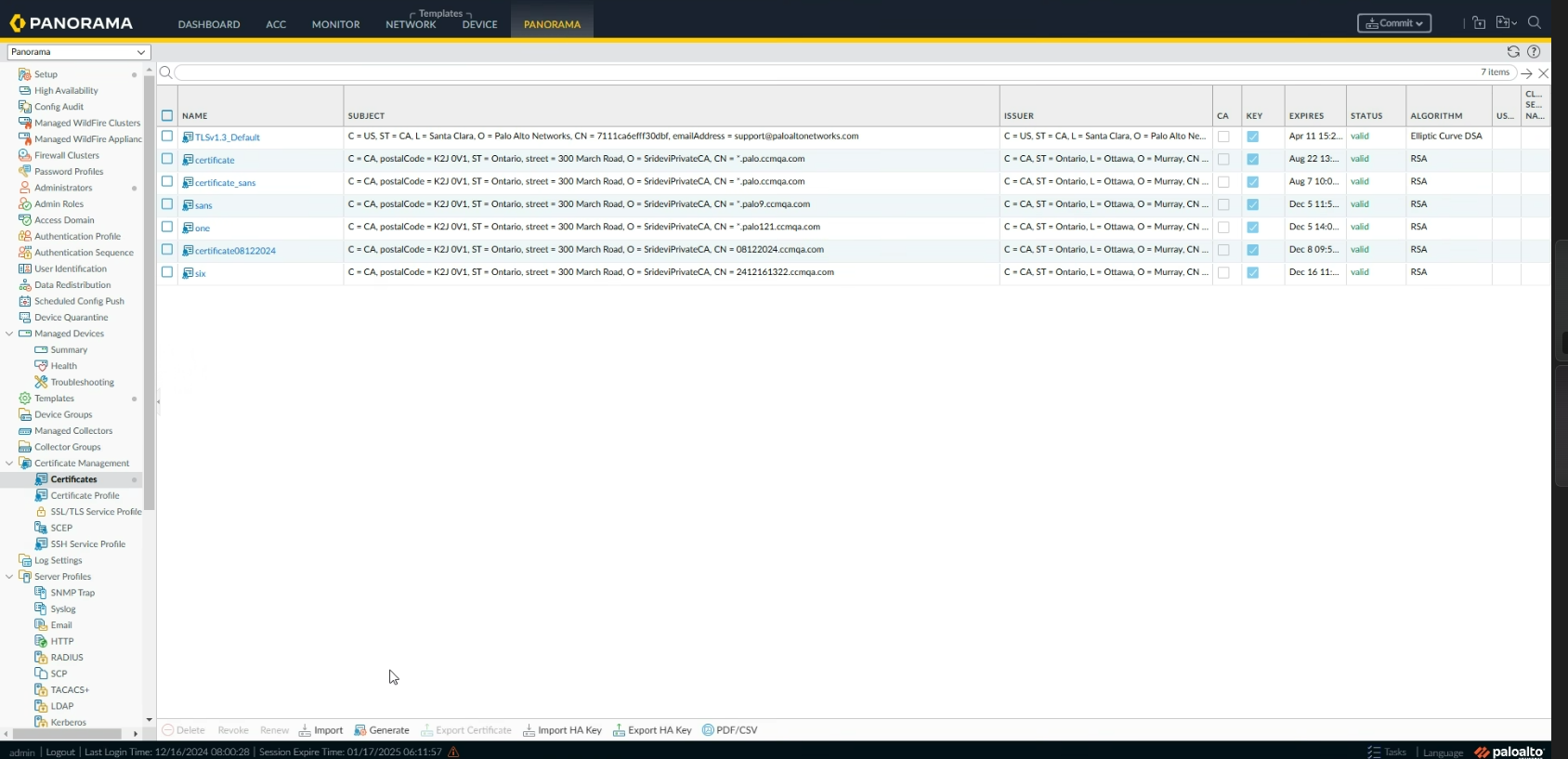
Using the connector
To list all possible options for the connector, run it with the --help option.
python3 paloaltoagent.py --helpEnroll a certificate
You can enroll for a specific certificate profile.
python3 paloaltoagent.py -a enroll -p <certificate>.yamlRenew a certificate
You can renew certificates for a specific certificate profile or for all certificate profiles available in the profile’s path.
python3 paloaltoagent.py -a renewpython3 paloaltoagent.py -a renew -p <certificate>.yamlEnable auto-renewal
You can create a cronjob that will invoke the connector on a schedule (see crontab for cron schedule expressions). To check the certificate’s eligibility for renewal, and if eligible, renew it:
-
Run
crontab -eon the terminal. -
Select an editor.
-
Add a cronjob that will trigger the connector.
The following example triggers
paloaltoagent.pyevery week. -
Save the changes and exit.
Replace a certificate
You can replace certificates, individually or in batches, for all certificate profiles available in the profile path. Each certificate profile file provides replacement information for one certificate.
Revoke a certificate
Certificate revocation is done manually in SCM. If a certificate is revoked in SCM, then during the next connector execution, the Sectigo CA server issues a new certificate, unless the certificate profile file has been removed. The connector imports the new certificate into the certificate management area of Palo Alto Firewall.
View the logs
The log files are stored in the location indicated in sectigo_log_path parameter of the config.yaml file.
By default, all events are recorded.
__main__ - INFO - Loading certificate profile cert1.yaml
paloaltofw.utils.sectigo_sops - DEBUG - Environment variable sectigo_gnu_key_store not defined. Getting fingerprint from the config file
paloaltofw.utils.sectigo_sops - DEBUG - File decrypted sectigo_credentials.yaml.
paloaltofw.utils.sectigo_sops - DEBUG - Environment variable sectigo_gnu_key_store not defined. Getting fingerprint from the config file
paloaltofw.utils.sectigo_sops - DEBUG - File decrypted fw_paloalto1.yaml.
...
__main__ - INFO - Certificate cert1 enrolled on SCM