Configuring the connector
This page describes how to configure the Sectigo connector, allowing you to manage certificates using Jira issues and workflows.
Obtain your SCM API credentials
You will need your SCM API credentials to configure the Sectigo Profile Settings in Jira.
-
Log in to SCM with the MRAO administrator credentials provided to your organization.
-
Select .
-
Select SSL Certificates REST API, and click Accounts.
-
Select your account and click Edit.
-
Click Reset Secret, and confirm resetting the client secret.
-
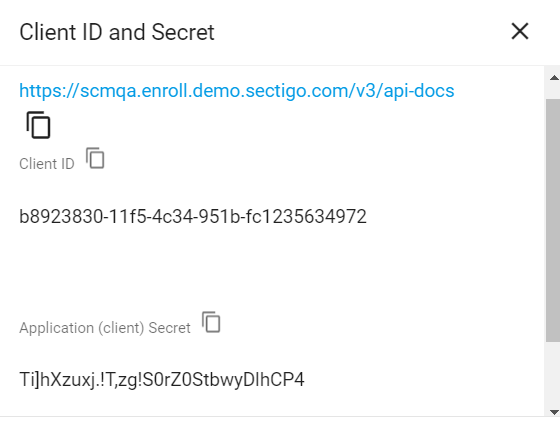
Make a copy of the values under Client ID and Application (client) Secret.
You will need to assign them to the Client ID and Client Secret parameters in Sectigo Profile Settings.
Configure Sectigo Profile Settings
Profile credentials are used to connect to data on the SCM Enrollment REST API.
| When the Sectigo plugin is installed, the Default User field is automatically set to the installing administrator’s username. This user identity is used for all automated certificate renewal jobs, but can be changed anytime in Profile Settings |
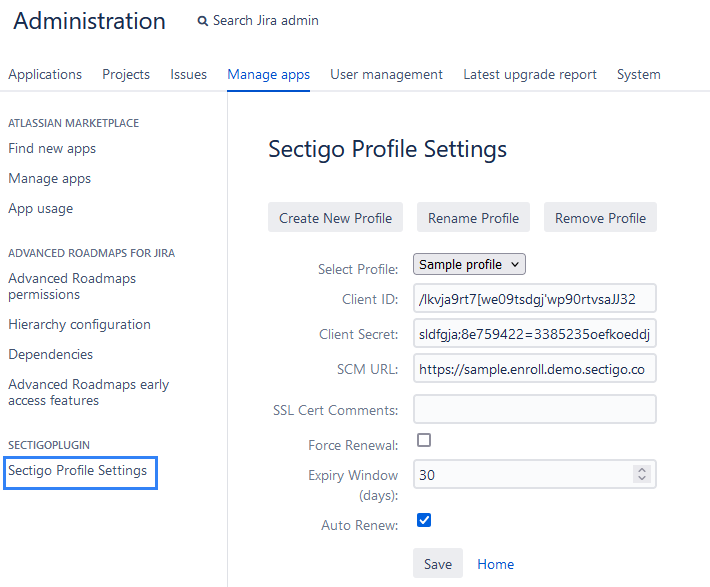
To create, rename, or remove a profile:
-
Navigate to Jira Administration, and select Manage Apps.
-
From the list of functions on the left side of the screen, select Sectigo Profile Settings.
-
Configure the profile settings based on the information in the following table.
Field Description Select Profile
Select an existing profile or create a new one.
Client ID
Your SCM client ID.
Client Secret
Your SCM client secret.
SCM URL
The URL of your SCM instance.
SSL Cert Comments
Optional comments.
Force Renewal
Select to force renewal of certificates for this profile within the next 24 hours.
Expiry Window (days)
Enter the number of days until the certificate expires. Not necessary if you selected Force Renewal.
Auto Renew
Select to automate certificate renewal before they expire. Not necessary if you selected Force Renewal.
-
Click Save.
Configure logging
-
Navigate to Jira Administration, and select System.
-
Under System Support, click Logging and profiling.
-
Scroll down to Default Loggers, and click Configure.
-
Enter com.sectigo, select INFO, and click Add.
Configure webhook for certificate expiry notification
This feature enables the Jira plugin to receive SSL certificate expiration notifications directly from SCM via webhook and automatically create a Jira issue in the Certificate Management Project.
SCM sends the webhook without authentication. The Jira server requires authentication to use the webhook URL.
There are two ways to get authentication:
-
Configure NGINX as a reverse proxy and add basic authentication for just the webhook endpoint.
Configure SCM to send webhook
-
Navigate to .
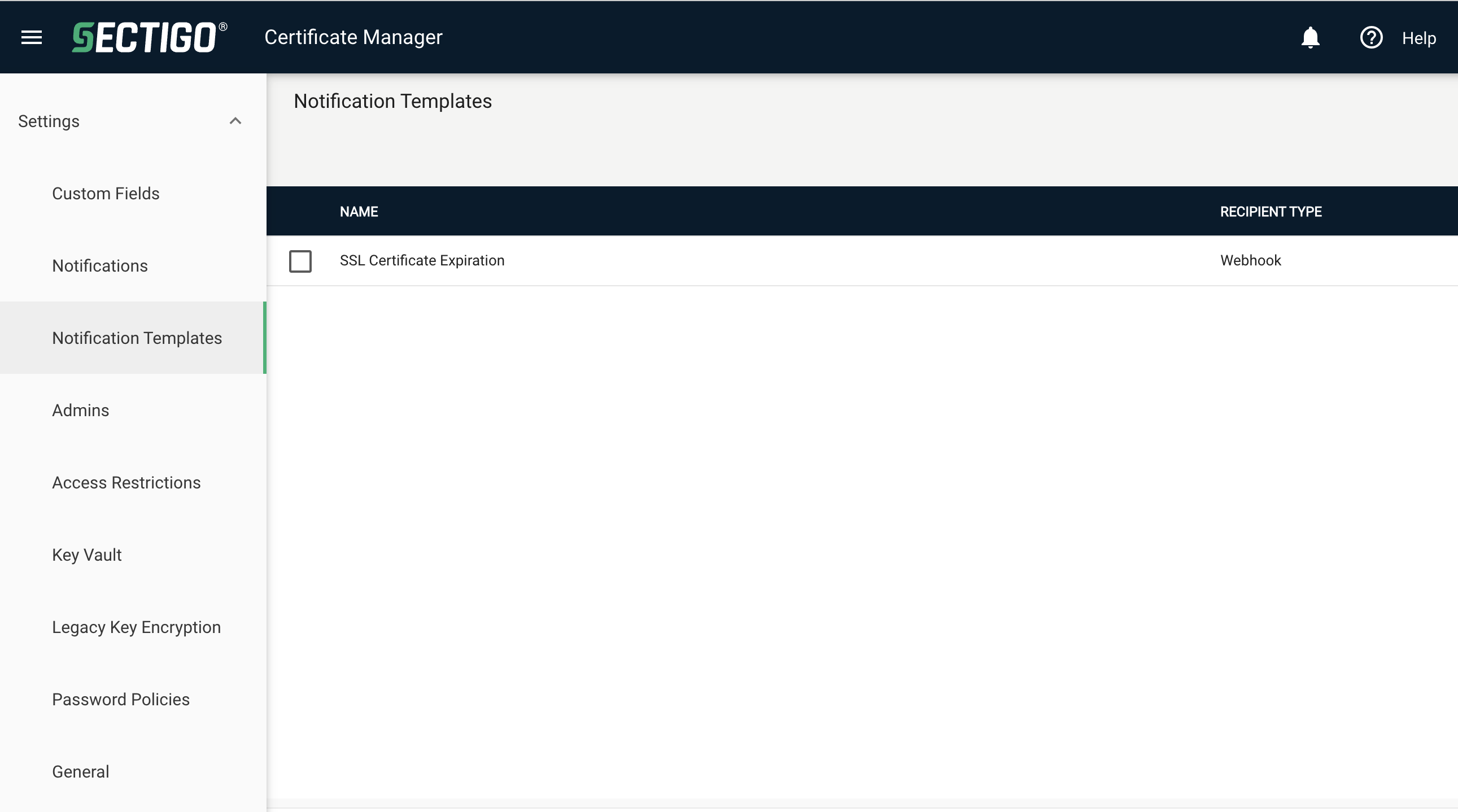
-
Click Add.
-
In Recipient Type, select Webhook.
-
In Notification Type, select SSL Certificate Expiration.
-
Click Next.
-
Select JSON.
-
Replace the existing text with the following:
{ "certificateId": "${certID}", "commonName": "${commonName}", "expirationDate": "${expiresDate}", "certificateComments": "${comments}", "certificateOrgDept": "${organization}/${department}", "certificateRequesterEmail": "${requesterEmail}" } -
Click Save.
-
Navigate to
-
In Name, enter a name for the notification.
-
Select Active.
-
In Notification Type, select SSL Certificate Expiration.
-
Click Next.
-
In the Recipients tab, click the plus sign to add Additional recipients.
-
Select type: Webhook.
-
In the Value field, enter the URL.
-
Click Next, then click Save.
Configure NGINX
The other way to get authentication for Jira to use the webhook URL is to configure NGINX as a reverse proxy which adds the authorization headers during requests.
If you are using a different web server, you can adapt the configuration accordingly using this NGINX example as a reference. You can also restrict public access to the URL and add rules to only allow requests coming from the SCM webhook. For more information, see your webserver documentation.
-
In your NGINX webserver, generate a base64 credential.
echo -n 'yourUser:yourPass' | base64 -
Configure NGINX as a reverse proxy and add basic authentication for just the webhook endpoint:
location /plugins/servlet/sectigo-notification-webhook {
proxy_pass http://localhost:8080;
proxy_set_header X-Real-IP $remote_addr;
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
proxy_set_header Host $host;
proxy_set_header X-Forwarded-Proto $scheme;
# Add Basic Authorization Header ONLY for this endpoint
proxy_set_header Authorization "Basic YWRtaW46YWRtaW4=";
}