Using the connector
This page describes how to use the connector with the AWS CLI and Amazon API Gateway.
|
If you’re getting a |
Using the connector with the AWS CLI
The following are example commands for enrolling and renewing certificates using the AWS CLI.
|
All examples of the Lambda function invocation in this document use AWS CLI v1.
However, you can also invoke the function with AWS CLI v2 by adding |
|
The Lamda function name uses the pattern "sectigoawscm-${terraform.workspace}-${random_pet.pet.id}". |
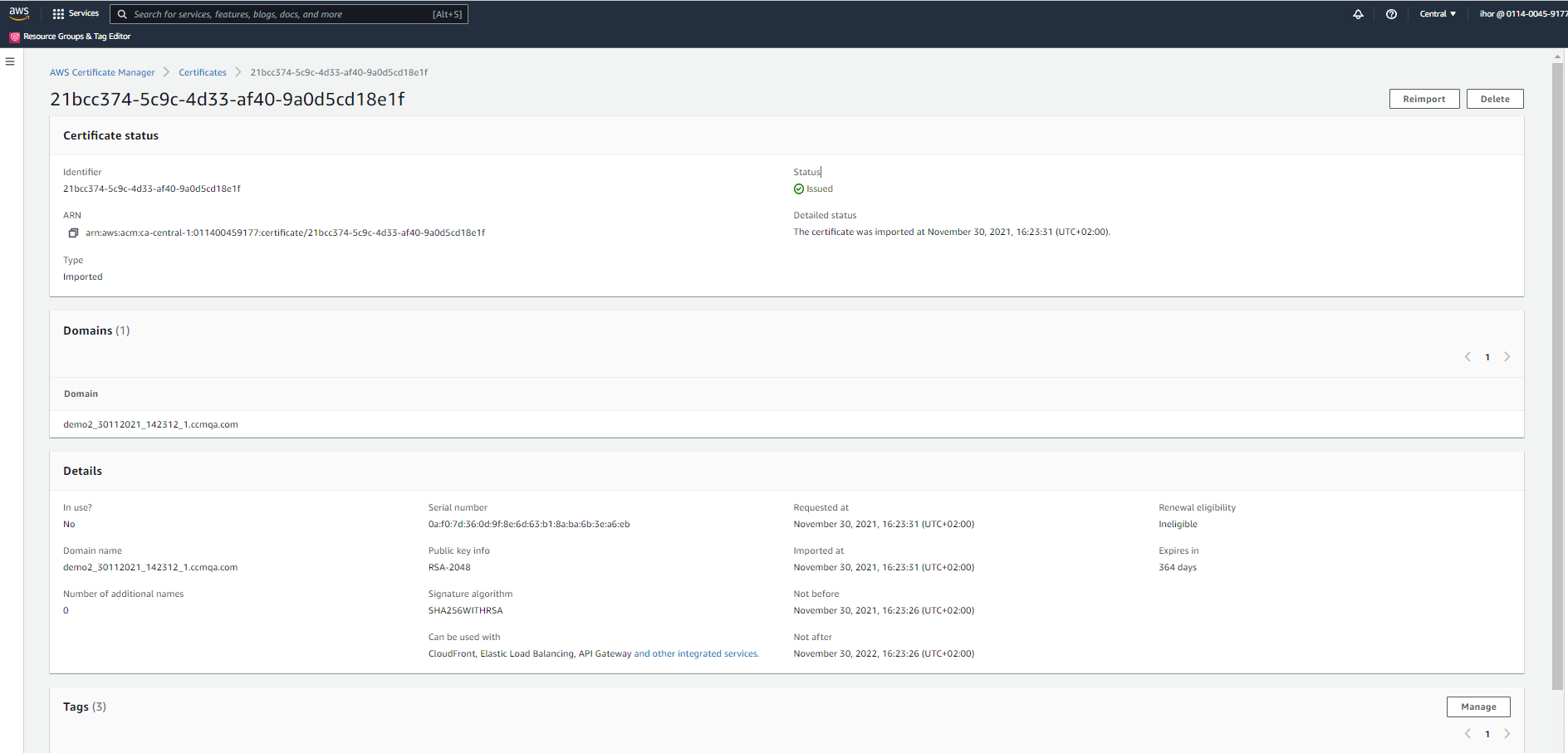
| If an attempt is made to enroll a certificate for a domain that already has a certificate, the ARN of the existing certificate will be returned. |
Enroll a single-domain certificate
You can use a specific AWS profile in AWS CLI (--profile <your_aws_profile>) or the default AWS profile.
|
aws lambda invoke --profile aws_account_1 --function-name sectigoawscm-multi-eu-central-1-pumped-lacewing \
--payload '{"domains": "ccmqa.com", "account": "scm_demo", "action": "enroll"}' \
response.jsonaws lambda invoke \
--profile multi \
--function-name sectigoawscm-multi-eu-central-1-stirred-hen \
--cli-binary-format raw-in-base64-out \
--payload "{\"domains\": \"aws.ccmqa.com\", \"account\": \"rsa_2048\", \"action\": \"enroll\", \"csrParameters\":{\"counry\": \"CA\", \"location\": \"Ottawa\", \"state\": \"Ontario\", \"organization\": \"SrideviPrivateCA\", \"sans\": \"san1.ccmqa.com, san2.ccmqa.com\"}}" response.jsonEnroll a multi-domain (SAN) or wildcard certificate
| If you use both options, all domains will be added to the SAN. |
aws lambda invoke --profile aws_account_1 --function-name sectigoawscm-multi-eu-central-1-pumped-lacewing \
--payload '{"domains": "*.ccmqa.com,d2.ccmqa.com,d3.ccmqa.com", \
"account": "scm_demo", "action": "enroll"}' \
response.jsonaws lambda invoke \
--profile multi \
--function-name sectigoawscm-multi-eu-central-1-stirred-hen \
--cli-binary-format raw-in-base64-out \
--payload "{\"domains\": \"aws.ccmqa.com\", \"account\": \"rsa_2048\", \"action\": \"enroll\", \"csrParameters\":{\"counry\": \"CA\", \"location\": \"Ottawa\", \"state\": \"Ontario\", \"organization\": \"SrideviPrivateCA\", \"sans\": \"san1.ccmqa.com, san2.ccmqa.com\"}}" response.jsonRenew revoked certificates for a specific ACME account
This command renews certificates created under a specific ACME account alias from the acme_accounts.yaml file.
aws lambda invoke --function-name sectigoawscm-multi-eu-central-1-pumped-lacewing \
--payload '{"account": "scm_demo", "action": "renew"}' \
response.jsonRenew revoked certificates for all ACME accounts
This command renews all certificates created under ACME account aliases from the acme_accounts.yaml file.
aws lambda invoke --profile aws_account_1 --function-name sectigoawscm-multi-eu-central-1-pumped-lacewing \
--payload '{"action": "renew"}' \
response.jsonRenew a specific certificate
To renew a specific certificate using its Amazon resource name (ARN):
aws lambda invoke --profile multi --function-name sectigoawscm-multi-eu-central-1-game-dragon \
--cli-binary-format raw-in-base64-out --payload "{ \"account\": \"action_name\", \"action\": \"renew\", \"arn\":\"arn:aws:acm:eu-central-1:011400459177:certificate/28771f49-947f-41d8-a507-0f0522bf0372\"}" response.json
Using the connector with API Gateway
The following are example commands for enrolling and renewing certificates using Amazon API Gateway (scroll right to view the full command).
| If you need to renew more than 30 certificates, use the connector with the AWS CLI. |
Enroll a single-domain certificate
curl --location --request GET \
'https://kxiinwdhxk.execute-api.ca-central-1.amazonaws.com/SectigoAWSCM/queries?domains=d1_124.ccmqa.com&account=scm_demo&action=enroll' \
--header 'x-api-key: GKIbu7ukcY4gRdahVK70x2lP4ANKMubJ2WBNHISG'Enroll a multi-domain (SAN) or wildcard certificate
curl --location --request GET \
'https://kxiinwdhxk.execute-api.ca-central-1.amazonaws.com/SectigoAWSCM/queries?domains=d1.ccmqa.com,d2.ccmqa.com&account=scm_demo&action=enroll' \
--header 'x-api-key: GKIbu7ukcY4gRdahVK70x2lP4ANKMubJ2WBNHISG'Renew revoked certificates for a specific ACME alias
This command renews certificates created under a specific ACME account alias from the acme_accounts.yaml file.
curl --location --request GET \
'https://kxiinwdhxk.execute-api.ca-central-1.amazonaws.com/SectigoAWSCM/queries?account=scm_demo&action=renew' \
--header 'x-api-key: GKIbu7ukcY4gRdahVK70x2lP4ANKMubJ2WBNHISG'Renew revoked certificates for all ACME aliases
This command renews all certificates created under ACME account aliases from the acme_accounts.yaml file.
curl --location --request GET \
'https://kxiinwdhxk.execute-api.ca-central-1.amazonaws.com/SectigoAWSCM/queries?action=renew' \
--header 'x-api-key: GKIbu7ukcY4gRdahVK70x2lP4ANKMubJ2WBNHISG'Notes
-
Duplicate certificates for a domain are not allowed under a single ACME account alias.
-
Multiple aliases can be defined for the same ACME account.
-
If you need different key sizes, you can create two aliases with the needed key sizes.
-
Make sure the signature algorithm of the server certificate matches the CA certificate. For example, the RSA server certificate must have the RSA CA chain, and the ECDSA server certificate must have the ECDSA CA chain.
Enable auto-renewal and logging using AWS CloudWatch
The Amazon Cloudwatch service allows you to create a cronjob that will invoke a Lambda function on a schedule. You can integrate CloudWatch with the connector to trigger the Lambda function that will check whether the certificate is eligible for renewal. For example, if you want to create a Cloudwatch event that will fire on the first day of every month, perform the following steps:
-
Sign in to the AWS EventBridge service.
-
Create a new rule.
-
Give a name to your rule, and specify a pattern and cron expression.
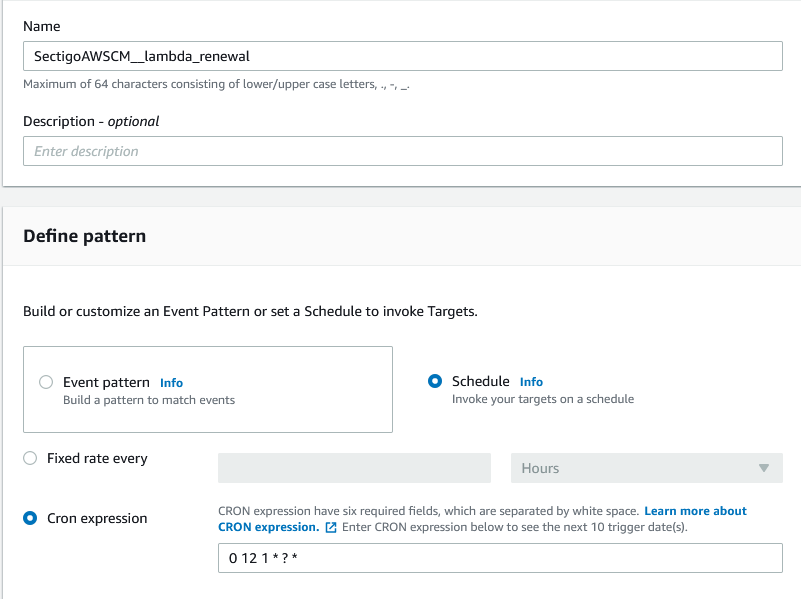
-
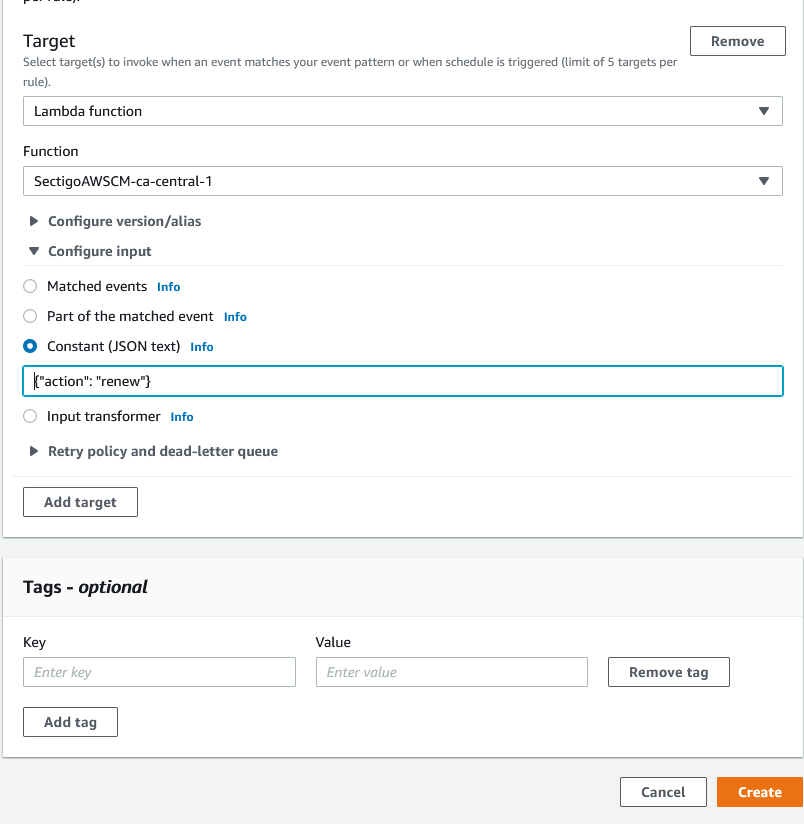
Select the Lambda function.
-
Specify the action.
-
Click Create to confirm the rule.
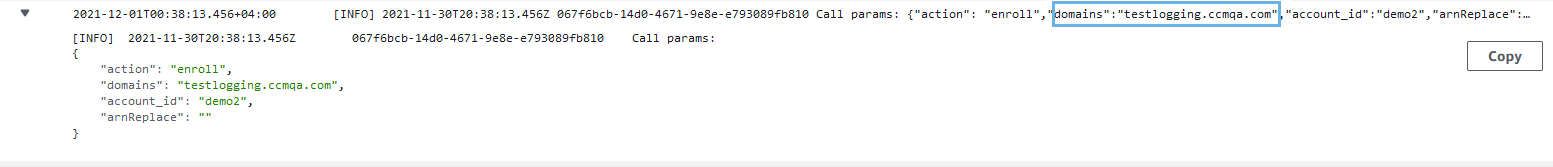
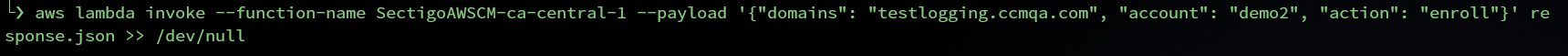
Cloudwatch log groups were created and integrated with Lambda when you executed the installation script. After the Lambda function is invoked, you can check the logs in AWS Cloudwatch. The following is an example of invoking a Lambda function and logging this event.
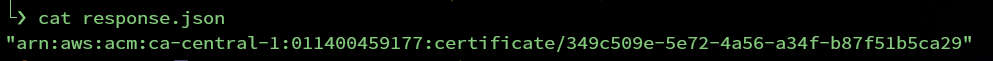
Visit the AWS CloudWatch console to view the logs.