Using the connector
This page provides commands for enrolling and managing certificates using the Akamai CPS CLI. Every time you run the connector to enroll or manage certificates, it checks whether all required tools and modules are installed on the system, and installs them if not found.
If you haven’t provided the execute permission to the connector, run the commands as follows.
bash certificate.sh <command>To list all possible commands and options, run the following command.
certificate.sh --helpEnroll a certificate
To enroll a certificate for a domain, specify the certificate profile file located in the ./domains/options directory.
certificate.sh enroll <domain_name>.yaml-
Uncomment the following lines in the
./domains/options/<domain_name.yamlfile and add SAN values.csr_sans: - example.com - www.example.com -
Run the connector with the domain name specified in the Common Name field.
certificate.sh enroll example.com
To enroll a wildcard certificate, add an asterisk and a dot (*.) before the domain name.
certificate.sh enroll *.example.comThe connector performs the following actions:
-
Collects values from the
./domains/options/<domain_name>.yamlfile and creates a./domains/yamls/<domain_name>.yamlfile.Don’t delete the
./domains/options/<domain_name>.yamlfile after enrolling a certificate. The connector uses this file for renewing the certificate. -
Sends an enrollment request to Akamai CPS using the information from the
./domains/yamls/<domain_name>.yamlfile. Akamai accepts this request and creates a certificate record in CPS. -
Downloads the CSR file from Akamai CPS.
-
Sends the CSR to SCM. SCM signs the CSR and generates a certificate and trust chain.
The agent also adds the SSL ID of the certificate (
certificate_id) to the./domains/options/<domain_name>.yamlfile. Don’t change this section in the file manually since it may break the renewal process. -
Downloads the certificate and trust chain files from SCM.
-
Uploads the certificate and trust chain files to Akamai CPS.
-
Deploys the certificate to the production environment on Akamai. The certificate cannot be used in production without this step.
Deploying a certificate on Akamai may take 10-15 minutes.
Possible errors include:
-
Invalid or empty values in the
./domains/options/<domain_name>.yamlor./domains/yamls/<domain_name>.yamlfile -
Authentication or authorization issues with the Sectigo API request
-
Akamai may take a long time to respond.
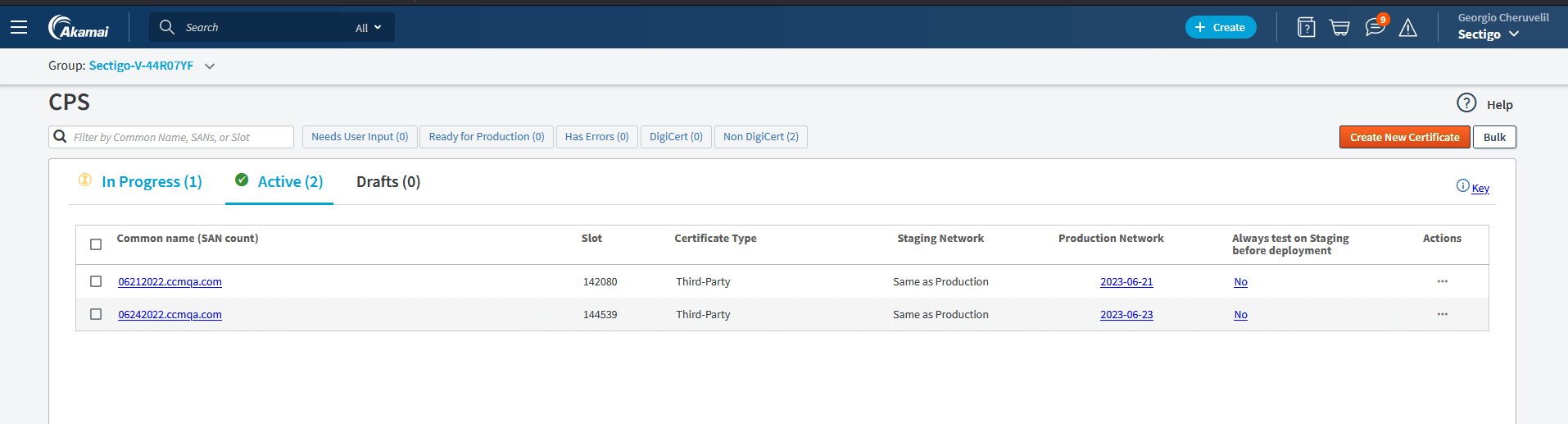
The following image shows provisioned certificates in Akamai CPS.
Renew a certificate
|
The |
certificate.sh renew-allcertificate.sh renew example.comRun the connector with the domain name that is specified in the Common Name field.
certificate.sh renew example.comTo renew a wildcard certificate, add an asterisk and a dot (*.) before the domain name.
certificate.sh renew *.example.comThe connector performs the following actions:
-
Checks whether the certificate and
./domains/yamls/<domain_name>.yamlfiles for this domain name exist. -
Checks the certificate revocation status: if the certificate is revoked, the connector informs you and force renews the certificate. If the certificate is not revoked, the connector checks whether the certificate is within the expiry window, and starts the renewal process. You can adjust the expiry window.
-
Updates the certificate status in Akamai CPS. The certificate status is updated with its
./domains/yamls/<domain_name>.yamlfile, then Akamai generates a new CSR. -
Downloads the CSR file from Akamai CPS.
-
Sends the CSR to SCM. SCM signs the CSR and generates a certificate and trust chain.
-
Downloads the certificate and trust chain files from SCM.
-
Uploads the certificate and trust chain files to Akamai CPS.
-
Deploys the certificate to the production environment on Akamai. The certificate cannot be used in production without this step.
Deploying a certificate on Akamai may take 10-15 minutes.
Possible errors include:
-
Missing certificate record for this domain
-
Invalid or empty values in the
./domains/options/<domain_name>.yamlor./domains/yamls/<domain_name>.yamlfile -
Authentication or authorization issues with the Sectigo API request
-
Akamai may take a long time to respond.
Enable auto-renewal
You can create a cronjob that will invoke the connector on a schedule to check whether the certificate is eligible for renewal:
-
Run
crontab -eon the terminal. -
Select an editor.
-
Add a cronjob that will trigger the connector.
The following examples trigger
certificate.shevery month.0 0 1 * * /home/ubuntu/sectigo-akamai-cm/certificate.sh renew-all0 0 1 * * /home/ubuntu/sectigo-akamai-cm/certificate.sh renew example.comRun the connector with the domain name that is specified in the Common Name field.
0 0 1 * * /home/ubuntu/sectigo-akamai-cm/certificate.sh renew example.comTo renew a wildcard certificate, add an asterisk and a dot (
*.) before the domain name.0 0 1 * * /home/ubuntu/sectigo-akamai-cm/certificate.sh renew *.example.com -
Save the crontab file.
Replace a certificate
The replace action updates an existing certificate with new attributes or values.
The validity period remains the same.
certificate.sh replacecertificate.sh replace example.comRun the connector with the domain name that is specified in the Common Name field.
certificate.sh replace example.comTo replace a wildcard certificate, add an asterisk and a dot (*.) before the domain name.
certificate.sh replace *.example.comThe connector performs the following actions:
-
Checks whether the certificate and
./domains/yamls/<domain_name>.yamlfiles for this domain name exist. -
Updates the certificate status in Akamai CPS. The certificate status is updated with its
./domains/yamls/<domain_name>.yamlfile, then Akamai generates a new CSR. -
Downloads the CSR file from Akamai CPS.
-
Sends the CSR to SCM for replacement. SCM signs the CSR and generates a certificate and trust chain.
-
Downloads the certificate and trust chain files from SCM.
-
Uploads the certificate and trust chain files to Akamai CPS.
-
Deploys the certificate to the production environment on Akamai. The certificate cannot be used in production without this step.
Deploying a certificate on Akamai may take 10-15 minutes.
Possible errors include:
-
Missing certificate record for this domain
-
Invalid or empty values in the
./domains/options/<domain_name>.yamlor./domains/yamls/<domain_name>.yamlfile -
Authentication or authorization issues with the Sectigo API request
-
Akamai may take a long time to respond.
List existing certificates
This command retrieves information on existing certificates from Akamai CPS.
List all certificates on Akamai CPS.
certificate.sh list --allView the details of a specific certificate.
certificate.sh list --details example.comList certificates deployed to production.
certificate.sh list --deployedList certificates enrolled, but not yet deployed.
certificate.sh list --enrolledDelete a certificate
To delete a certificate from Akamai CPS, run the following command.
certificate.sh delete example.comThe connector deletes the following files:
-
The certificate from Akamai CPS (this might take a few hours)
-
The
./domains/options/<domain_name>.yamlfile from the local machine -
The
./domains/yamls/<domain_name>.yamlfile from the local machine -
The
./logs/<domain_name>.logfile from the local machine