Additional notes
Understanding certs and fetch paths
The certs path implemented in the Sectigo Vault PKI plugin allows you to read, delete, or list certificates that are already stored in Vault under the given config name.
The fetch path gives you the ability to download certificates from SCM, that are not already stored in Vault, and to store them on your Vault server.
If a user attempts to fetch a certificate that already exists in Vault, the behavior of the command will be the same as reading a certificate through path certs.
Certificate renewal flow diagram
The following diagram illustrates a typical certificate renewal scenario using the Sectigo Vault PKI plugin.
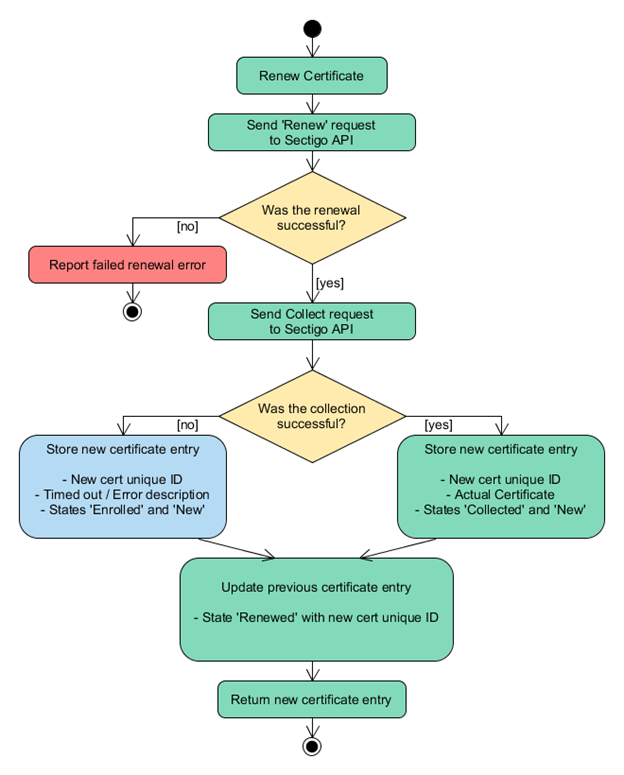
Understanding path profile
The profile path implemented in the Sectigo Vault PKI plugin allows you to obtain, read, delete, or list profile information stored in Vault under the given config name and profile ID.
Profile information is downloaded from SCM using the sectigo_ssl_cert_type or sectigo_client_cert_type field as the sectigo_profile_unique_id.
The sectigo_cm_org_id can be provided for optimization of profile downloads.
Once the profile is downloaded, whenever an enrollment or replacement occurs, the certificate profile fields are verified with the corresponding certificate fields prior to the request being transmitted to SCM.
Replacement with profile verification requires the sectigo_ssl_cert_type or sectigo_client_cert_type field provided with the request.
{
"request_id": "<request_id>",
"lease_id": "",
"renewable": false,
"lease_duration": 0,
"data": {
"description": "<sectigo_profile_description>",
"id": <sectigo_profile_unique_id>,
"keyTypes": {
"EC": [
<ECDSA_curve_array>
],
"RSA": [
<RSA_bits_length_array>
]
},
"name": "<profile_name>",
"terms": [
<terms_array>
],
"useSecondaryOrgName": false
},
"wrap_info": null,
"warnings": null,
"auth": null
} "keyTypes": {
"EC": [
"P-384"
],
"RSA": [
"2048",
"3072",
"4096",
"8192"
]
},
"terms": [
365,
730,
1095
],