Using the connector
This page describes how to use the connector to search and monitor the audit logs.
Search for logs
-
In Splunk Web, select .
-
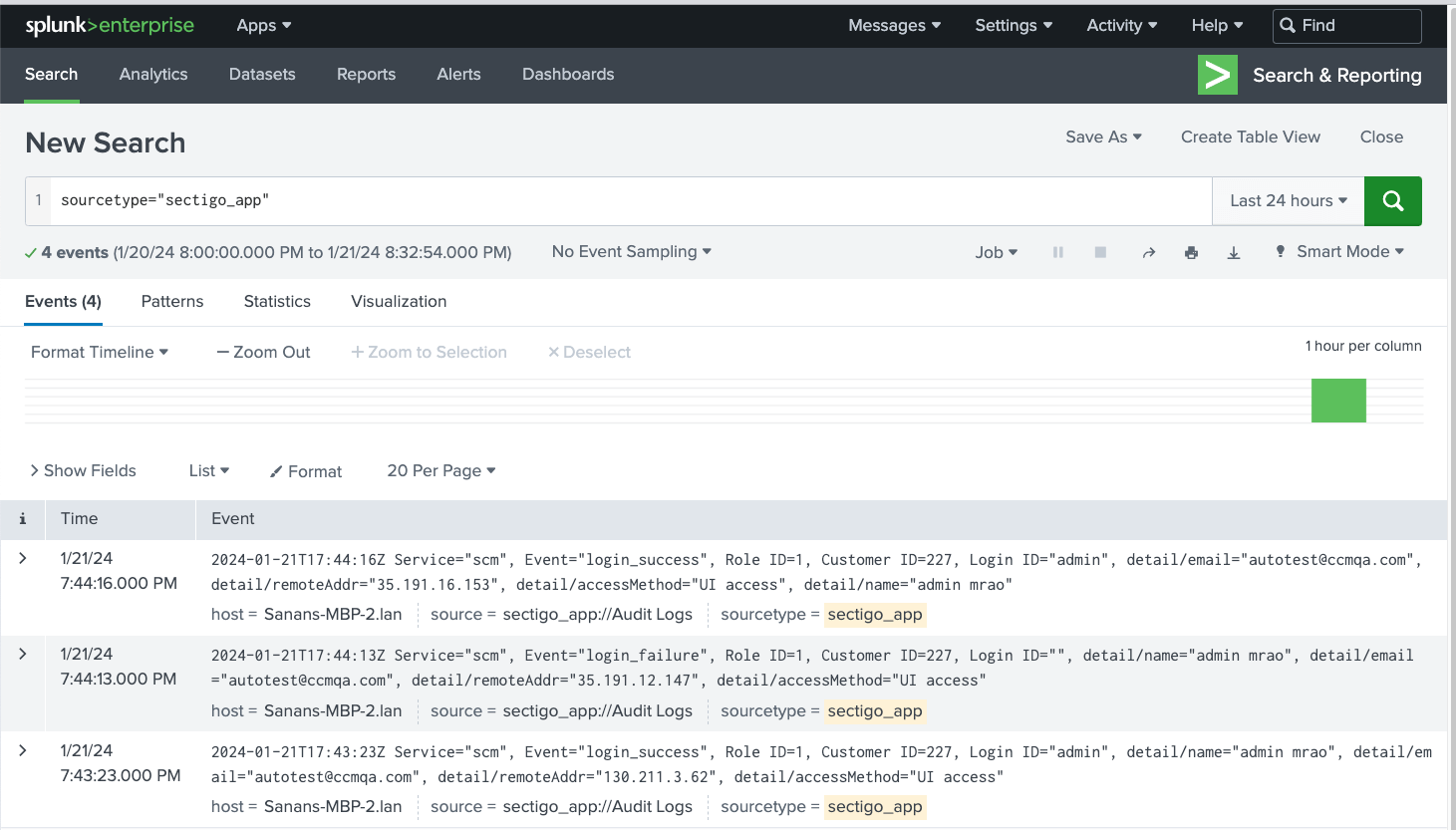
In the Search field, enter your search term or regular expression to search for certain logs. You might experience a delay of up to a minute before you see the data.
To view all logs pertaining to SCM without duplicates, enter
sourcetype="sectigo_app | dedup _raw". For example, to retrieve only failed login attempts, addEvent="login_failure".The following list includes the main fields from the SCM Audit API response:
-
Service: The name of the service that generated an audit event
-
Event: The action that was performed
-
Login ID: The person that performed the action
-
Customer ID: The ID of the customer who owns the audit logs
-
Details/*: The event-specific details
-