Using the connector
This page describes how to use the connector to search and monitor the audit logs on the Azure portal.
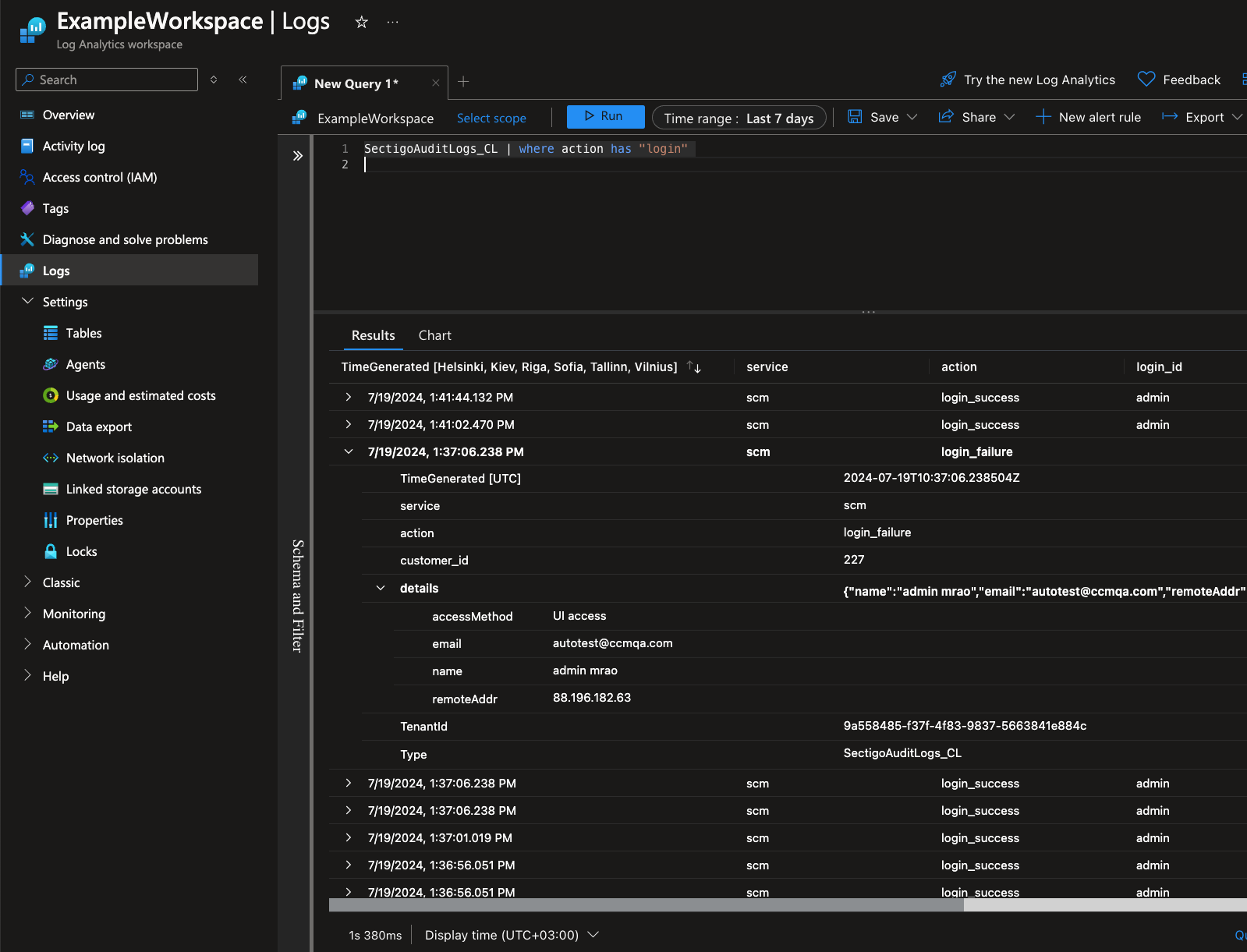
Query Sectigo Audit Logs
-
From the Azure portal, navigate to Log Analytics Workspace > Logs.
-
Select a time range.
-
Query Sectigo audit logs within the given time range, by entering a KQL command. This table lists some examples.
Action Query Return audit logs for the given time range
SectigoAuditLogs_CLReturn audit logs for the given time range where logins were successful
SectigoAuditLogsTable_CL | where action == "login_success"Return audit logs for the given time range where logins failed
SectigoAuditLogsTable_CL | where action == "login_failure"Return audit logs from the last hour where logins failed
SectigoAuditLogsTable_CL | where action == "login_failure" and TimeGenerated>= ago(1h)Return audit logs with the word "certificate" in any column
SectigoAuditLogs_CL | where * has 'certificate'
It is usual to experience a delay (5-30 minutes) for the first log entries to be available in the Log Analytics workspace.
If you see a no results found message, try again a bit later.
|
| Find more about KQL queries here: Kusto Query Language (KQL) overview. |