Using the connector
This page describes how to use the connector to automate the certificate lifecycle on LoadMaster load balancers.
|
To view all available options, run |
|
Make sure that the command |
Enroll a certificate
You can enroll certificates individually or in batches—for all certificate profiles available in the profile path. Each certificate profile file provides enrollment information for one certificate.
| You need to accept the EULA agreement when you use the connector for the first time. |
Verify SSL enablement
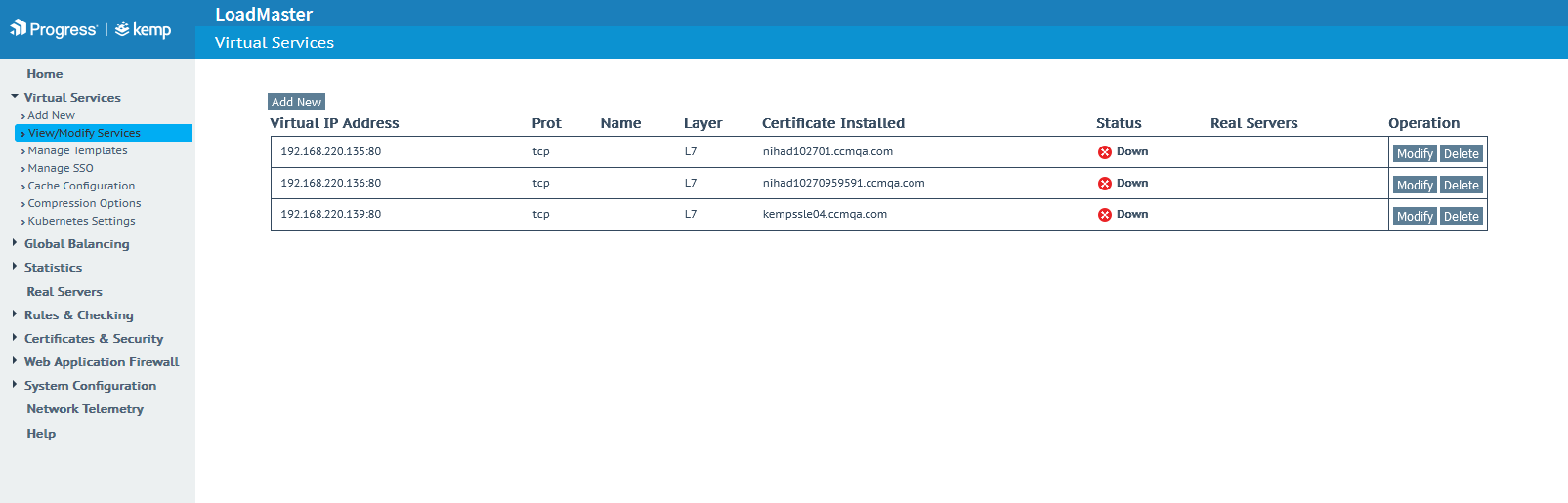
To verify that the certificate has been installed to the virtual server, navigate to . The Certificate Installed column displays the certificate attached to the respective virtual IP address.
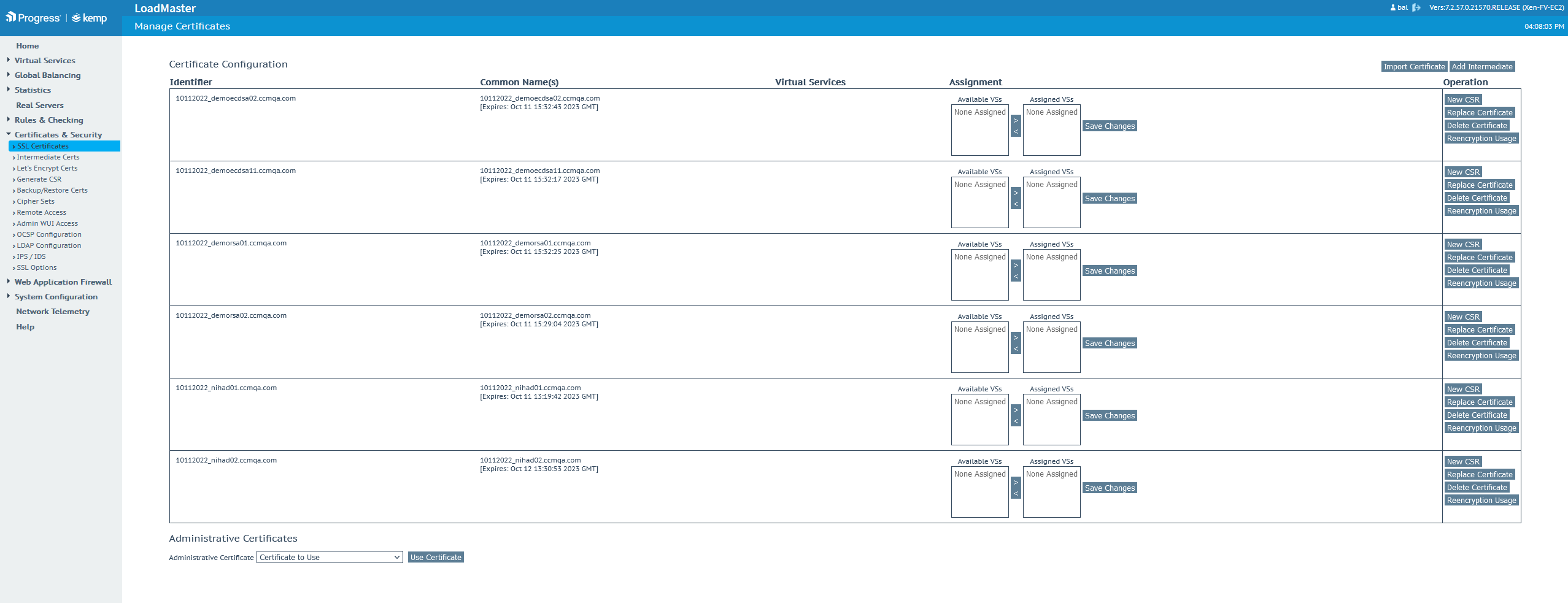
To view the provisioned certificate(s) in the LoadMaster’s SSL management area, navigate to .
Renew a certificate
You can renew certificates individually or in batches—for all certificate profiles available in the profile path. Each certificate profile file provides renewal information for one certificate.
|
The |
Renew certificates for all profiles.
python3 main.py -a renewRenew certificates for individual profiles.
python3 main.py -a renew -p <cert_profile_1.yaml> [,<cert_profile_2.yaml>]Enable auto-renewal
You can create a cronjob that will invoke the script on a schedule (see crontab for cron schedule expressions) to check the certificate expiry status and renew it if expired:
-
Run
crontab -eon the terminal. -
Add a cronjob that will trigger the script.
The following example will trigger
main.pyevery week. -
Save the changes and exit.
Replace a certificate
You can replace certificates individually or in batches—for all certificate profiles available in the profile path. Each certificate profile file provides replacement information for one certificate.
Revoke a certificate
Certificate revocation is done manually in SCM. If a certificate is revoked in SCM, then during the next connector execution, the Sectigo CA server issues a new certificate, unless the certificate profile file has been removed.
List certificates
You can retrieve a list of provisioned certificates from LoadMaster.
Retrieve certificates for all Kemp profiles.
python3 main.py -a listRetrieve certificates for individual Kemp profiles.
python3 main.py -a list -p <kemp_profile_1.yaml> [,<kemp_profile_2.yaml>][
{
"profile_name":"cert_profile_ecdsa1",
"exist":"True",
"csr_domain":"10112022_demoecdsa11.ccmqa.com",
"not_valid_before":"2022-10-11 15:32:17",
"not_valid_after":"2023-10-11 15:32:17",
"ocsp_status":"GOOD",
"ssl_cert_subject_alt_names":"san1.ccmqa.com,san2.ccmqa.com"
},
...
]View the logs
The log files are stored in the location indicated in the log_path parameter of the config.yaml file.
By default, all events are recorded.
2023-01-31 15:44:55,444 - __main__ - INFO - --------------------------------------------------
2023-01-31 15:44:55,447 - config.models.CertificateProfile - INFO - Loading certificate profile : cert_profile_1.yaml
2023-01-31 15:44:55,450 - utils.yaml_encrypt - INFO - Encrypted property doesn't exist in the file. File: kemp_profile_1.yaml is not encrypted
2023-01-31 15:44:55,451 - utils.yaml_encrypt - INFO - Encrypted property doesn't exist in the file. File: scm.yaml is not encrypted
...
2023-01-31 15:44:58,528 - root - DEBUG - response code: 200, {"certId":"eyJpZCI6Mzg4NzgsInR5cGUiOiJTU0wifQ=="}
2023-01-31 15:44:58,529 - root - DEBUG - enrollment succeed