Using the connector
This page describes how to use the Google Cloud Platform (GCP)connector with the Google Cloud CLI or with an HTTPS request.
Google cloud function actions
The two major functions you can perform using the connector are enrolling and renewing certificates. Using either Google Cloud CLI or HTTPS, you can enroll or renew SSL certificates and add them to Google Cloud Certificate Manager.
You can enroll a single domain, or multi-domain (SAN) or wildcard certificate by using different parameters in the payload file.
Use the csr_domain parameter for:
-
single domain
-
wildcard domain
Use the csr_domain and ssl_cert_subject_alt_names parameters for:
-
multi-domain (SAN)
-
wildcard domain in SAN
Certificates can be assigned to a specific region or regions, or globally, using the cert_region parameter.
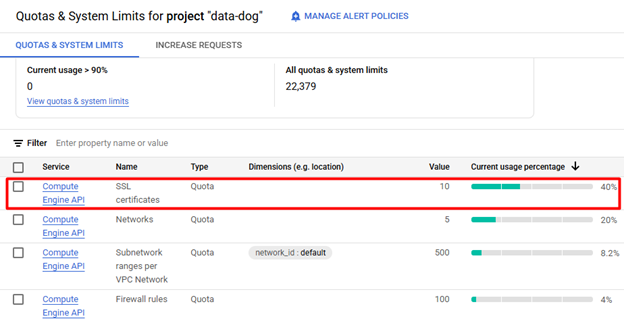
SSL certificate quota
Before enrollment or renewal the quota for SSL certificates is checked. By default, GCP allows enrolling or renewing of up to 10 certificates. If you need more than 10 certificates, contact GCP support.
When Quota SSL_CERTIFICATES is exceeded, execution stops.
In the current implementation, during renew if you have 10 certificates in GCP CM and would like to renew all of them then your Quota SSL_CERTIFICATES must be 20 certificates to make successful renewal possible.
Metric name = compute.googleapis.com/ssl_certificates
Limit name = SSL-CERTIFICATES-per-project
For more information, see https://cloud.google.com/compute/quotas.
Enroll a certificate
Enrollment parameters
The parameters of the gcloud function payload file are described in the following table.
| Parameter | Description |
|---|---|
|
Performed action. In this case use |
|
A name for your account. In the examples that follow we use |
|
Used to define regional SSL certificates. If this field is absent then region defaults to GLOBAL. |
|
The |
|
|
|
The domain included in the certificate Common Name (CN) field. This field is used to enroll a single-domain certificate. |
|
The country name in the certificate Country © field. |
|
The state or province in the certificate State (ST) field. |
|
The locality name in the certificate Locality (L) field. |
|
The organization name in the certificate Organization (O) field. |
|
The email address in the certificate Email Address field. |
|
The key algorithm to use for certificate enrollment.
The possible values are |
|
The key size to use for certificate enrollment. The possible values are: RSA: ECDSA: |
|
Comments for certificate enrollment. |
|
The comma-separated list of subject alternative names (SAN) for the certificate. This field is used to enroll a mult-domain or wildcard certificate. |
|
Certificate validity period in days. |
|
Number of days prior to expiration that the certificate’s renewal process is initiated. |
|
Whether the certificate should renew automatically. Options are |
|
If you’re getting a 200 status code response, but the connector isn’t performing the requested operation, there is probably a syntax error in your |
Enroll a single-domain certificate using CLI
You can enroll a single domain certificate by using the csr_domain and not using the ssl_cert_subject_alt_names parameter.
Certificates can be assigned to a specific region or regions, or globally, dictated by the cert_region parameter.
In these examples we use the account name ENROLL_API_ACCOUNT, which was created in Customize the scm.yaml file > Enrollment API.
gcloud functions call --gen2 sectigogcpcm-us-central1-agcpf --data '{
"action": "enroll",
"account": "ENROLL_API_ACCOUNT",
"cert_profile": {
"ssl_cert_comments": "coments test with Enrollment API",
"csr_domain": "your.domain",
"ssl_cert_subject_alt_names": "",
"ssl_cert_validity": 365,
"csr_country": "",
"csr_state": "",
"csr_location": "",
"csr_organization": "",
"csr_email_address": "",
"csr_key_type": "RSA",
"csr_key_size": 2048,
"force_renewal": true,
"expiry_window": 30,
"auto_renew": true
}
}' --format=json --region=us-central1gcloud functions call --gen2 sectigogcpcm-us-central1-agcpf --data '{
"action": "enroll",
"account": "ENROLL_API_ACCOUNT",
"cert_region": "europe-central2,africa-south1",
"cert_profile": {
"ssl_cert_comments": "coments test with Enrollment API",
"csr_domain": "your.domain",
"ssl_cert_subject_alt_names": "",
"ssl_cert_validity": 365,
"csr_country": "",
"csr_state": "",
"csr_location": "",
"csr_organization": "",
"csr_email_address": "",
"csr_key_type": "RSA",
"csr_key_size": 2048,
"force_renewal": true,
"expiry_window": 30,
"auto_renew": true
}
}' --format=json --region=us-central1Enroll a single-domain certificate using HTTPS
curl -X POST -H "Authorization: Bearer $(gcloud auth print-identity-token)" \
'https://us-central1-local-project-340815.cloudfunctions.net/SectigoGCP-us-central1' \
-H "Content-Type:application/json" \
--data '{
"action": "enroll",
"account": "ENROLL_API_ACCOUNT",
"cert_profile": {
"ssl_cert_comments": "coments test with Enrollment API",
"csr_domain": "your.domain",
"ssl_cert_subject_alt_names": "",
"ssl_cert_validity": 365,
"csr_country": "",
"csr_state": "",
"csr_location": "",
"csr_organization": "",
"csr_email_address": "",
"csr_key_type": "RSA",
"csr_key_size": 2048,
"force_renewal": true,
"expiry_window": 30,
"auto_renew": true
}
}'curl -X POST -H "Authorization: Bearer $(gcloud auth print-identity-token)" \
'https://us-central1-local-project-340815.cloudfunctions.net/SectigoGCP-us-central1' \
-H "Content-Type:application/json" \
--data '{
"action": "enroll",
"account": "ENROLL_API_ACCOUNT",
"cert_region": "europe-central2,africa-south1",
"cert_profile": {
"ssl_cert_comments": "coments test with Enrollment API",
"csr_domain": "your.domain",
"ssl_cert_subject_alt_names": "",
"ssl_cert_validity": 365,
"csr_country": "",
"csr_state": "",
"csr_location": "",
"csr_organization": "",
"csr_email_address": "",
"csr_key_type": "RSA",
"csr_key_size": 2048,
"force_renewal": true,
"expiry_window": 30,
"auto_renew": true
}
}'Enroll a multi-domain (SAN) or wildcard certificate using CLI
You can enroll a multi-domain (SAN) or wildcard certificate using the csr_domain and ssl_cert_subject_alt_names parameter.
Certificates can be assigned to a specific region or regions, or globally, dictated by the cert_region parameter.
In these examples we use the account name ENROLL_API_ACCOUNT, which was created in Customize the scm.yaml file > Enrollment API.
gcloud functions call --gen2 sectigogcpcm-us-central1-agcpf --data '{
"action": "enroll",
"account": "ENROLL_API_ACCOUNT",
"cert_profile": {
"ssl_cert_comments": "coments test with Enrollment API",
"csr_domain": "your.domain",
"ssl_cert_subject_alt_names": "san1.ccmqa.com, *.san2.ccmqa.com",
"ssl_cert_validity": 365,
"csr_country": "",
"csr_state": "",
"csr_location": "",
"csr_organization": "",
"csr_email_address": "",
"csr_key_type": "RSA",
"csr_key_size": 2048,
"force_renewal": true,
"expiry_window": 30,
"auto_renew": true
}
}' --format=json --region=us-central1gcloud functions call --gen2 sectigogcpcm-us-central1-agcpf --data '{
"action": "enroll",
"account": "ENROLL_API_ACCOUNT",
"cert_region": "europe-central2,africa-south1",
"cert_profile": {
"ssl_cert_comments": "coments test with Enrollment API",
"csr_domain": "your.domain",
"ssl_cert_subject_alt_names": "san1.ccmqa.com, *.san2.ccmqa.com",
"ssl_cert_validity": 365,
"csr_country": "",
"csr_state": "",
"csr_location": "",
"csr_organization": "",
"csr_email_address": "",
"csr_key_type": "RSA",
"csr_key_size": 2048,
"force_renewal": true,
"expiry_window": 30,
"auto_renew": true
}
}' --format=json --region=us-central1Enroll a multi-domain (SAN) or wildcard certificate using HTTPS
In these examples we use the account name ENROLL_API_ACCOUNT, which was created in Customize the scm.yaml file > Enrollment API.
curl -X POST -H "Authorization: Bearer $(gcloud auth print-identity-token)" \
'https://us-central1-local-project-340815.cloudfunctions.net/SectigoGCP-us-central1' \
-H "Content-Type:application/json" \
--data '{
"action": "enroll",
"account": "ENROLL_API_ACCOUNT",
"cert_profile": {
"ssl_cert_comments": "coments test with Enrollment API",
"csr_domain": "your.domain",
"ssl_cert_subject_alt_names": "san1.ccmqa.com, *.san2.ccmqa.com",
"ssl_cert_validity": 365,
"csr_country": "",
"csr_state": "",
"csr_location": "",
"csr_organization": "",
"csr_email_address": "",
"csr_key_type": "RSA",
"csr_key_size": 2048,
"force_renewal": true,
"expiry_window": 30,
"auto_renew": true
}
}'curl -X POST -H "Authorization: Bearer $(gcloud auth print-identity-token)" \
'https://us-central1-local-project-340815.cloudfunctions.net/SectigoGCP-us-central1' \
-H "Content-Type:application/json" \
--data '{
"action": "enroll",
"account": "ENROLL_API_ACCOUNT",
"cert_region": "europe-central2,africa-south1",
"cert_profile": {
"ssl_cert_comments": "coments test with Enrollment API",
"csr_domain": "your.domain",
"ssl_cert_subject_alt_names": "san1.ccmqa.com, *.san2.ccmqa.com",
"ssl_cert_validity": 365,
"csr_country": "",
"csr_state": "",
"csr_location": "",
"csr_organization": "",
"csr_email_address": "",
"csr_key_type": "RSA",
"csr_key_size": 2048,
"force_renewal": true,
"expiry_window": 30,
"auto_renew": true
}
}'Renew a certificate
Renew parameters
The renew parameters are described in the following table.
| Parameter | Description |
|---|---|
|
Performed action. In this case use |
|
A name or label for your account. This field is optional if you specify |
|
The unique identifier assigned to a specific certificate. You must specify at least one of |
|
Used to define regional SSL certificates. If this field is absent then region defaults to GLOBAL. |
|
If you’re getting a 200 status code response, but the connector isn’t performing the requested operation, there is probably a syntax error in your |
Renew specific certificates using CLI
When you renew a certificate, you can change some of the details.
gcloud functions call --gen2 sectigogcpcm-us-central1-agcpf --data '{"action":"renew", "cert_name":"cert20250616115607597314"}' --format=jsongcloud functions call --gen2 sectigogcpcm-us-central1-agcpf --data '{"action":"renew" , "cert_region": "europe-central2", "cert_name":"cert20250616115607597314"}' --format=jsonRenew all certificates for a specific account with CLI
When you renew a certificate, you can change some of the details.
In these examples we use the account name ENROLL_API_ACCOUNT, which was created in Customize the scm.yaml file > Enrollment API.
gcloud functions call --gen2 sectigogcpcm-us-central1-agcpf --data '{"action":"renew","account":"ENROLL_API_ACCOUNT}' --format=jsongcloud functions call --gen2 sectigogcpcm-us-central1-agcpf --data '{"action":"renew","account":"ENROLL_API_ACCOUNT" , "cert_region": "europe-central2"}' --format=jsonRenew specific certificates using HTTPS
curl -X POST -H "Authorization: Bearer $(gcloud auth print-identity-token)" \
'https://us-central1-local-project-340815.cloudfunctions.net/SectigoGCP-us-central1' \
-H "Content-Type:application/json" \
--data '{"action":"renew","account":"ENROLL_API_ACCOUNT"}'curl -X POST -H "Authorization: Bearer $(gcloud auth print-identity-token)" \
'https://us-central1-local-project-340815.cloudfunctions.net/SectigoGCP-us-central1' \
-H "Content-Type:application/json" \
--data '{"action":"renew","account":"ENROLL_API_ACCOUNT"}' \
--region=us-central1Renew all certificates using HTTPS
curl -X POST -H "Authorization: Bearer $(gcloud auth print-identity-token)" \
'https://us-central1-local-project-340815.cloudfunctions.net/SectigoGCP-us-central1' \
-H "Content-Type:application/json" \
--data '{"action":"renew"}'curl -X POST -H "Authorization: Bearer $(gcloud auth print-identity-token)" \
'https://us-central1-local-project-340815.cloudfunctions.net/SectigoGCP-us-central1' \
-H "Content-Type:application/json" \
--data '{"action":"renew"}' \
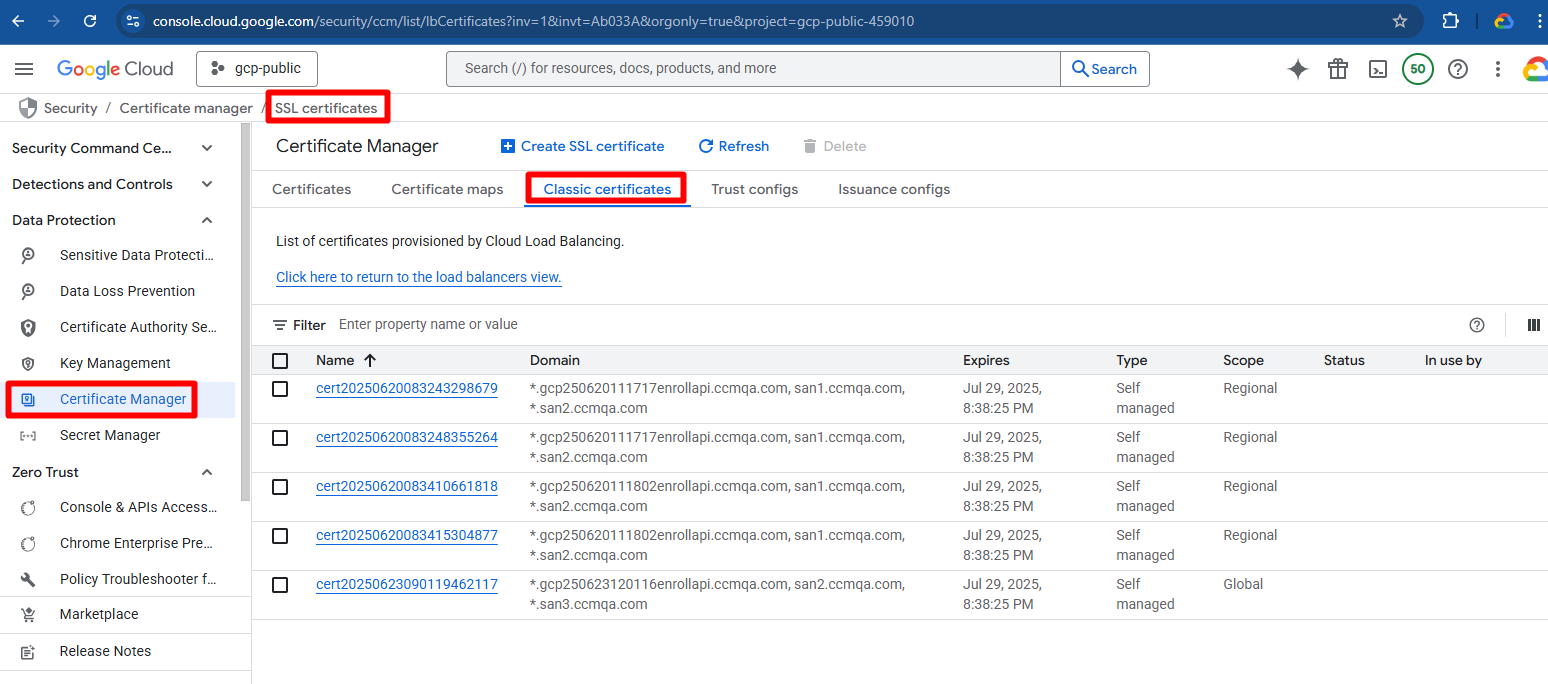
--region=us-central1View certificates on Google console
To view your certificates on GCP, navigate to Google Cloud Console > Certificate Manager.
Attaching certificates to load balancers
The SectigoGCPCM_https_lb_example and SectigoGCPCM_ssl_lb_example archives contain sample Terraform configuration for provisioning and attaching certificates to external HTTP(S) load balancers and SSL proxy load balancers.
Add the external data source configuration to your main Terraform module.
The data source triggers the enroll.sh script that calls the Cloud Function to enroll a certificate and attach it to the target proxy for the load balancer.
The README.md file in the archive provides instructions on using the external data source.
The following is a sample data source configuration.
// Data source for enrolling a certificate
data "external" "example" {
program = ["/bin/bash","./enroll.sh","sectigohttpslb.ccmqa.com"]
}
output cert_name {
value = "${data.external.example.result.result}"
}
// Target HTTPS proxy for the load balancer
resource "google_compute_target_https_proxy" "default" {
depends_on = [
data.external.example
]
name = "example-target-proxy"
url_map = google_compute_url_map.default.id
ssl_certificates = ["${data.external.example.result.result}"]
}