Using the connector
This page describes how to use the connector to automate the certificate lifecycle on vThunder software appliances.
|
To view all available options, run |
|
Make sure that the command |
Enroll a certificate
You can enroll certificates individually or in batches—for all certificate profiles available in the profile path. Each certificate profile file provides enrollment information for one certificate.
| You need to accept the EULA agreement when you use the connector for the first time. |
Enroll certificates for all profiles.
python3 main.py -a enrollEnroll certificates for individual profiles.
python3 main.py -a enroll -p <cert_profile_1.yaml> [,<cert_profile_2.yaml>]Enroll with ACME
You can also enroll a certificate through the UI—vThunder provides native support for certificate enrollment using the ACME protocol.
| ACME is supported natively since vThunder 5.2.1-p5, build 114. |
To enroll a certificate:
-
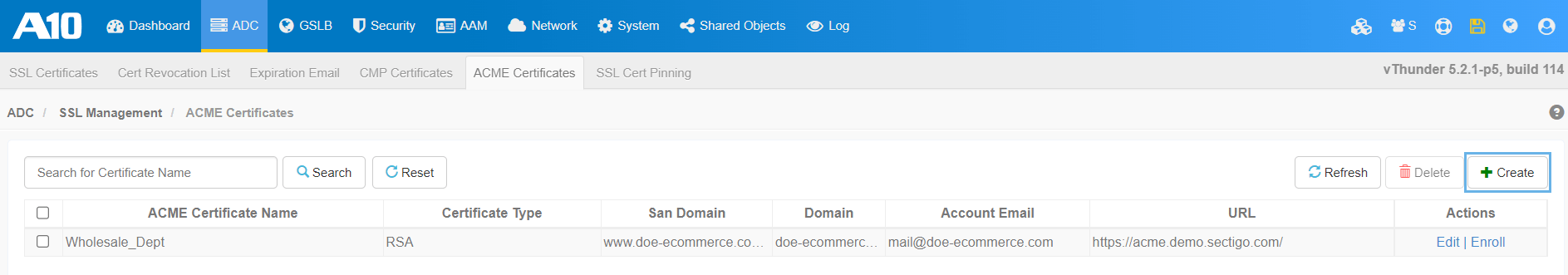
Select .
-
Select the ACME Certificates tab.
-
Click Create to configure a certificate profile.
-
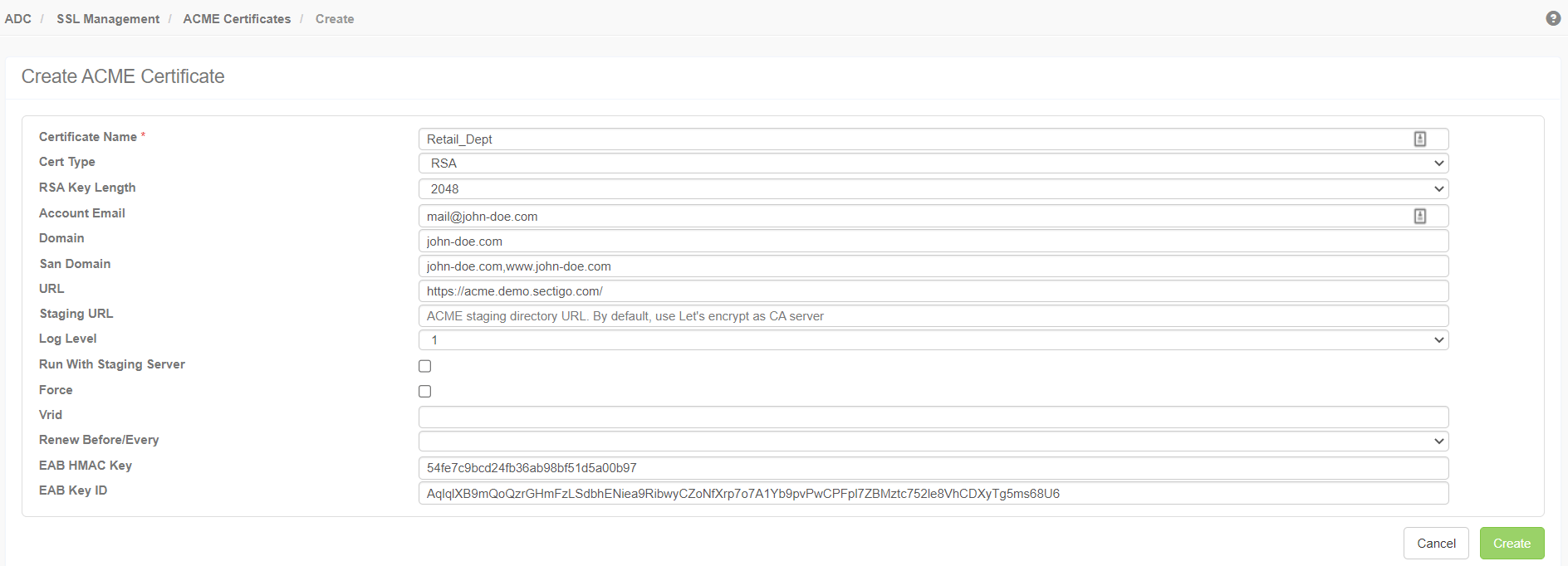
Complete the fields and click Create to save the profile.
-
Click Enroll to provision a certificate.
Verify SSL enablement
To verify that the certificate has been attached to the virtual server:
-
Navigate to .
-
Select the virtual server.
-
Click Edit.
-
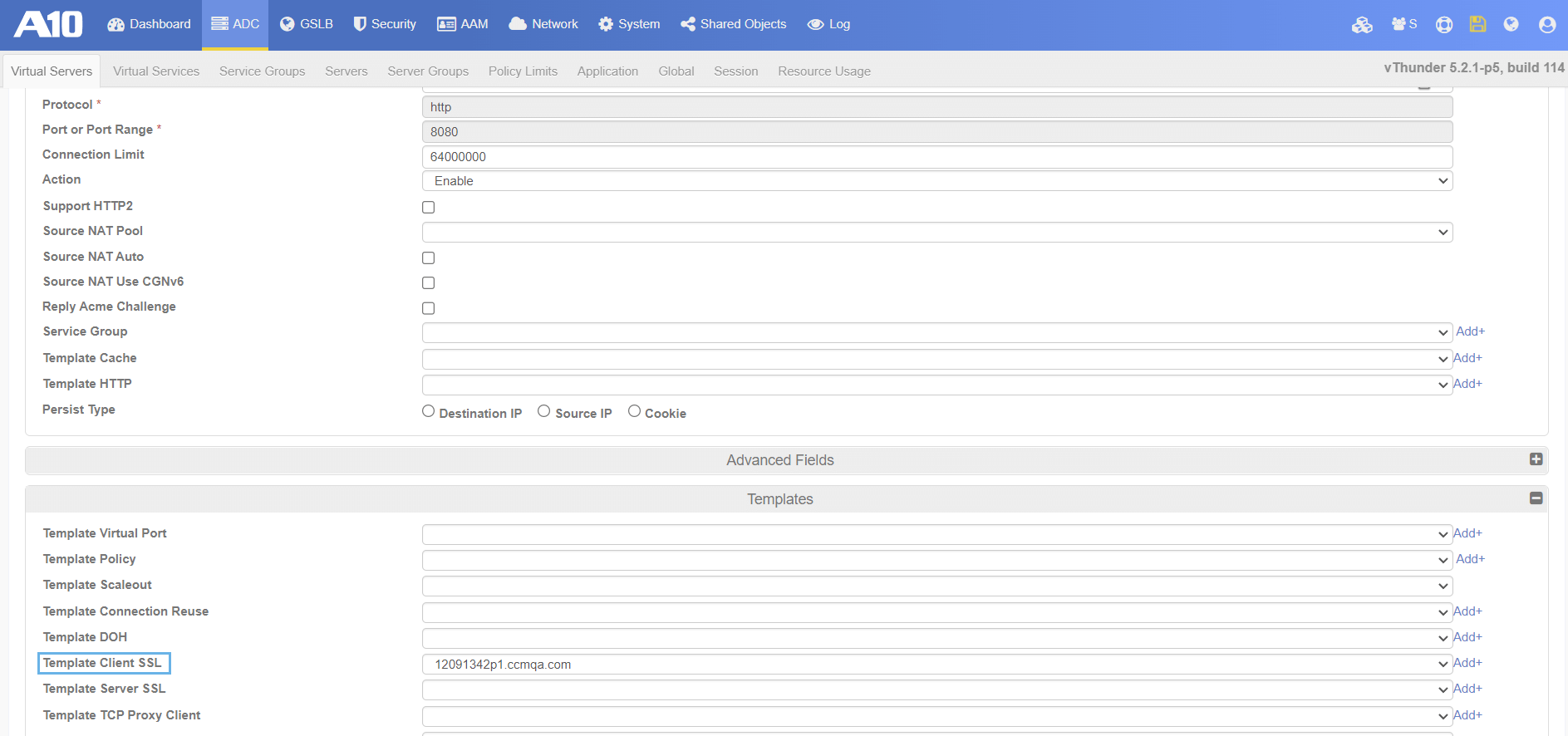
Extend the Templates section.
-
The Template Client SSL field should specify the client SSL template bound to the virtual server.
The client SSL template contains keys and certificates for SSL-encrypted traffic between clients and the ACOS device.
-
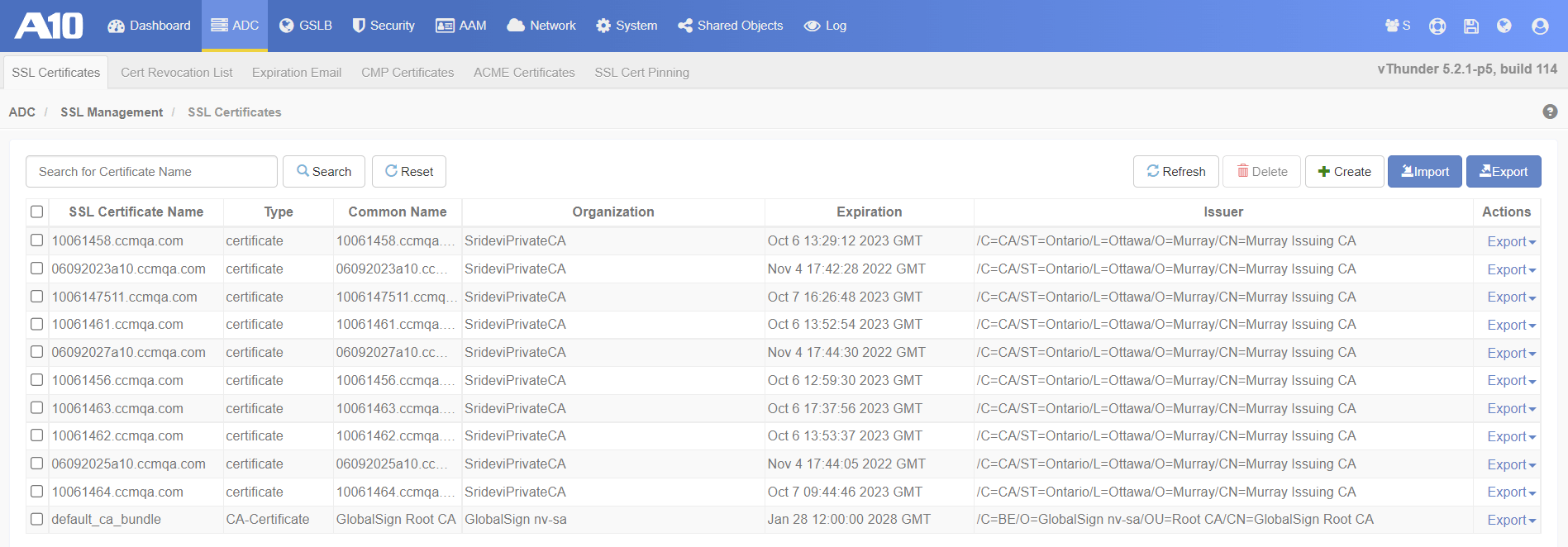
(Optional) To view the provisioned certificate(s) in the vThunder SSL management area, navigate to .
Renew a certificate
You can renew certificates individually or in batches—for all certificate profiles available in the profile path. Each certificate profile file provides renewal information for one certificate.
|
The The |
Renew certificates for all profiles.
python3 main.py -a renewRenew certificates for individual profiles.
python3 main.py -a renew -p <cert_profile_1.yaml> [,<cert_profile_2.yaml>]Enable auto-renewal
You can create a cronjob that will invoke the script on a schedule (see crontab for cron schedule expressions) to check the certificate expiry status and renew it if expired:
-
Run
crontab -eon the terminal. -
Add a cronjob that will trigger the script.
The following example will trigger
main.pyevery week. -
Save the changes and exit.
Replace a certificate
You can replace certificates individually or in batches—for all certificate profiles available in the profile path. Each certificate profile file provides replacement information for one certificate.
Revoke a certificate
Certificate revocation is done manually in SCM. If a certificate is revoked in SCM, then during the next connector execution, the Sectigo CA server issues a new certificate, unless the certificate profile file has been removed.
List certificates
You can retrieve a list of provisioned certificates from vThunder.
Retrieve certificates for all A10 profiles.
python3 main.py -a listRetrieve certificates for individual A10 profiles.
python3 main.py -a list -p <a10_profile_1.yaml> [,a10_profile_2.yaml][
{
"name":"10061458.ccmqa.com",
"type":"certificate",
"serial":"0x40FD846FF04EA9ADFF0599B84CEDA3DC",
"notbefore":"Oct 6 13:29:12 2022 GMT",
"notafter":"Oct 6 13:29:12 2023 GMT",
"common-name":"10061458.ccmqa.com",
"organization":"SrideviPrivateCA",
"subject":"/C=CA/postalCode=K2J 0V1/ST=Ontario/street=300 March Road/O=SrideviPrivateCA/CN=10061458.ccmqa.com",
"issuer":"/C=CA/ST=Ontario/L=Ottawa/O=Murray/CN=Murray Issuing CA",
"notafter-number":1696598952,
"status":"[Unexpired, Unbound]"
},
...
]View the logs
The log files are stored in the location indicated in the log_path parameter of the config.yaml file.
By default, all events are recorded.
2023-01-17 19:22:47,319 - third_party.a10_provider - INFO - Getting cert by name in A10 Networks
2023-01-17 19:22:47,320 - urllib3.connectionpool - DEBUG - Starting new HTTPS connection (1): ec2-15-223-14-57.ca-central-1.compute.amazonaws.com:443
2023-01-17 19:22:47,873 - urllib3.connectionpool - DEBUG - https://ec2-15-223-14-57.ca-central-1.compute.amazonaws.com:443 "GET /axapi/v3/file/ssl-cert/01171922p1.ccmqa.com HTTP/1.1" 404 157
...
2023-01-17 19:22:51,617 - root - DEBUG - response code: 200, {"certId":"eyJpZCI6Mzg2NTcsInR5cGUiOiJTU0wifQ=="}
2023-01-17 19:22:51,617 - root - DEBUG - enrollment succeed