Configuring the connector
This page describes how to configure the connector to automate the certificate lifecycle management for Akamai.
Authenticate with Akamai
Create an .edgerc file in your home directory (~/.edgerc) with the secret, access_token, host, and client_token information for authentication through EdgeGrid.
To generate the credentials:
-
Log in to the Control Center.
-
Select your profile at top right, then select User settings on the Users tab.
-
Click Create API client, then click Quick or Advanced.
-
Copy the values to an
.edgercfile in your home directory.[default] client_secret = A113nt53KF3TM6N90yVuAgICgIRwsObLi0E67/N8eRN= host = akab-h05tnam3wl42son7nktnlnnx-kbob3i3v.luna.akamaiapis.net access_token = akab-acc35t3k3nokujqunph3w0hzp7-gtq6ij client_token = akab-c111ntt3k3n4qtari202bfxxbsl-yksej -
Add a pointer to your
.edgercfile in the provider block of yourakamai.tffile.provider "akamai" { edgerc = "~/.edgerc" config_section = "default" }
For more details, see Add authentication in Akamai documentation.
Obtain your SCM API credentials
You will need your SCM API credentials to configure the Sectigo Profile Settings in Akamai.
-
Log in to SCM with the MRAO administrator credentials provided to your organization.
-
Select .
-
Select SSL Certificates REST API, and click Accounts.
-
Select your account and click Edit.
-
Click Reset Secret, and confirm resetting the client secret.
-
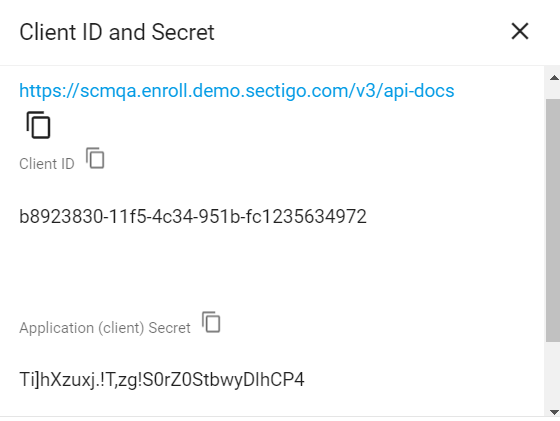
Make a copy of the values under Client ID and Application (client) Secret.
You will need to assign them to the Client ID and Client Secret parameters in Sectigo Profile Settings.
Set up the config file
Configure the scm_config.yaml file.
client_id: "e9a4a344-eafd-471d-a9cb-496835ffcb76"
client_secret: "e9a4a344-eafd-471d-a9cb-496835ffcb76"
scm_url: https://scmqa.enroll.demo.sectigo.comThe following table describes parameters in the file.
| Parameter | Description |
|---|---|
|
The client ID of the SCM user. |
|
The client secret of the SCM user. |
|
The URL of the SCM account. |
Set up additional certificate fields
To include non-CSR fields in the certificate, (e.g., external requester, comments, custom fields), use the additional_fields.yaml file located in the example folder.
For examples of how to format, see the additional_fields_example.yaml file.
Configure Terraform
Configure the Terraform variables in the ./module/variables.tf file and/or example/main.tf file.
Refer to the table below.
-
If you have only one domain, you can edit the
variables.tffile and remove the./example/main.tffile. -
If you have two or more domains, create a directory for each domain and copy the
./example/main.tffile to those directories.The
./example/main.tffile contains only a handful of variables, such as the domain name or key type. It’s assumed that most certificate attributes will have the same values, which can be defined in thevariables.tffile. If you need custom values for each domain, you can add more variables to./example/main.tf, which will override the default values fromvariables.tf.
The following table describes the variables that you need to configure for certificate issuance.
Some of them will likely have values defined on a per-certificate basis (for example, SAN values), while for others you may want to define default values in the variable.tf file (for example, the contact details of the Akamai administrator).
For a full list of available variables and their values, see DV third-party enrollment.
| Variable | Description |
|---|---|
|
The Akamai contract ID. |
|
The domain name included in the certificate Common Name (CN) field. |
|
A comma-separated list of subject alternative names (SAN) included in the certificate subjectAltName field. |
|
The certificate signing request (CSR) information.
|
|
The key algorithm to use for certificate enrollment. The possible values are:
|
|
The network information and TLS metadata. |
|
The details of the organization. |
|
The details of the Akamai administrator contact at your company. |
|
The details of the certificate administrator contact at your company. |
|
The number of days prior to expiration that a certificate renewal process is initiated.
|
|
If set to Default: |
|
Enables Server Name Indication (SNI) for the enrollment. Default: |